Master Remoteiot: Access IoT Devices Behind Firewalls (No Windows OS!)
Are you ready to unlock the full potential of your Internet of Things (IoT) devices, even when they're hidden behind firewalls and scattered across the globe? The ability to remotely access and manage your IoT devices is no longer a futuristic fantasy; it's a practical necessity, and this guide provides the roadmap to make it happen.
Remote access to IoT devices is transforming the way we interact with technology. It's about more than just convenience; it's about efficiency, control, and the ability to respond proactively to the needs of your connected devices. Imagine the possibilities: controlling your smart home from your office, troubleshooting industrial sensors from a remote location, or monitoring connected vehicles in real-time. The potential is limitless, and the key lies in understanding how to securely and effectively establish these remote connections.
Before diving into the technical aspects, let's consider the fundamental value proposition of IoT remote access. It empowers you to control and monitor your devices from virtually any location with an internet connection. This capability enhances productivity by eliminating the need for on-site visits, reduces operational costs through proactive maintenance and remote diagnostics, and provides a layer of convenience that simplifies the management of a diverse array of connected devices. Moreover, remote access allows for quick responses to critical alerts, ensuring the smooth operation of your IoT ecosystem and minimizing downtime. It's about staying connected, informed, and in control, no matter where you are.
The world of IoT is rapidly expanding, encompassing everything from smart home appliances to complex industrial systems. As these devices become more prevalent, the need for secure and efficient remote access becomes paramount. This guide is designed to be your companion on that journey, equipping you with the knowledge and tools necessary to navigate the challenges and embrace the opportunities of remote IoT management.
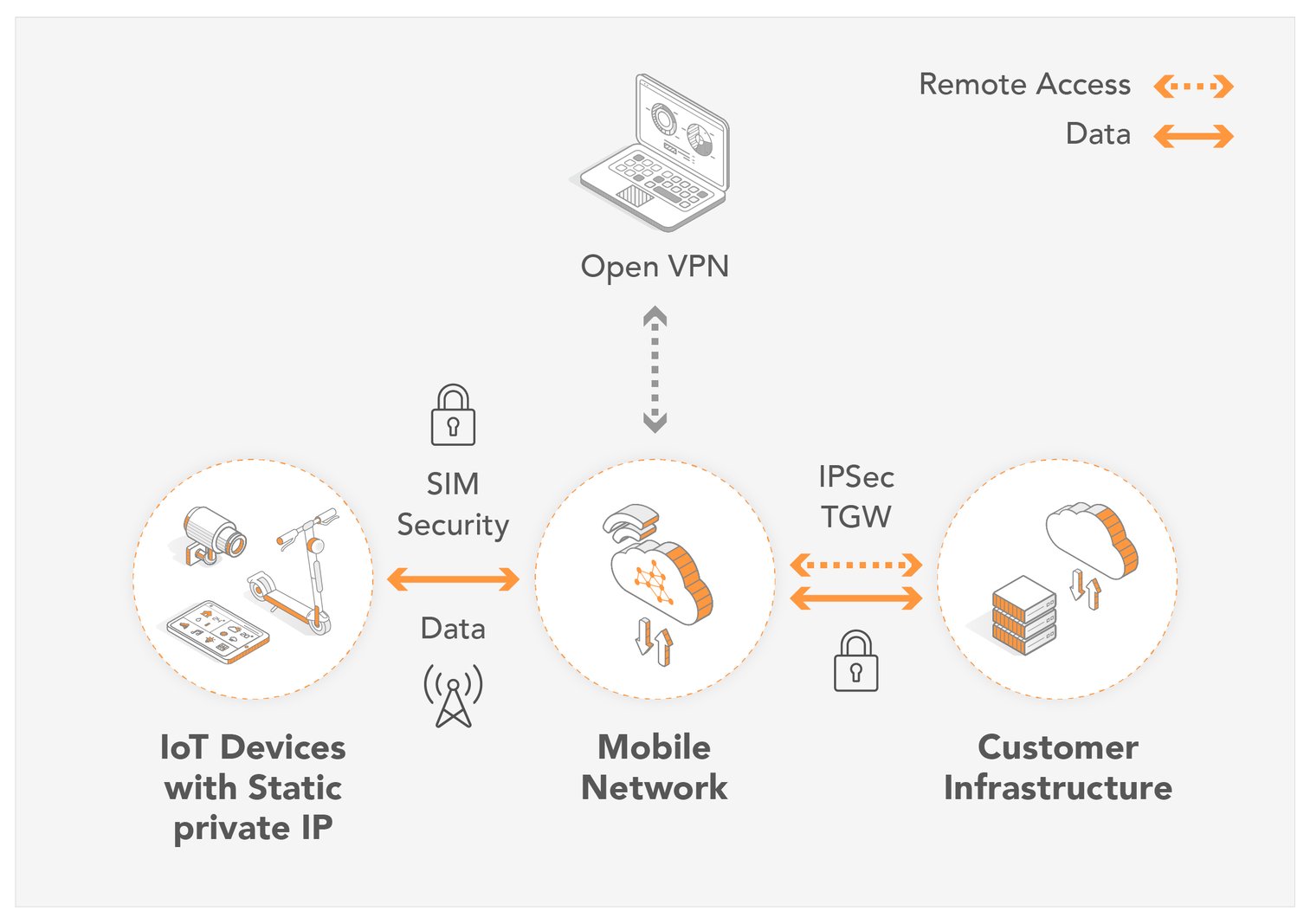
One of the most critical aspects of setting up remote access is securing your devices. This involves several key steps, including changing default passwords and usernames to prevent unauthorized access, implementing robust encryption protocols such as TLS or DTLS to protect all network traffic, and configuring firewalls to restrict access to specific IP addresses and only allow the required traffic. Additionally, using a VPN connection for remote access to the IoT network can provide an extra layer of security, creating a secure tunnel for all communications. This multi-layered approach ensures that your devices are protected from potential threats and that your data remains confidential.
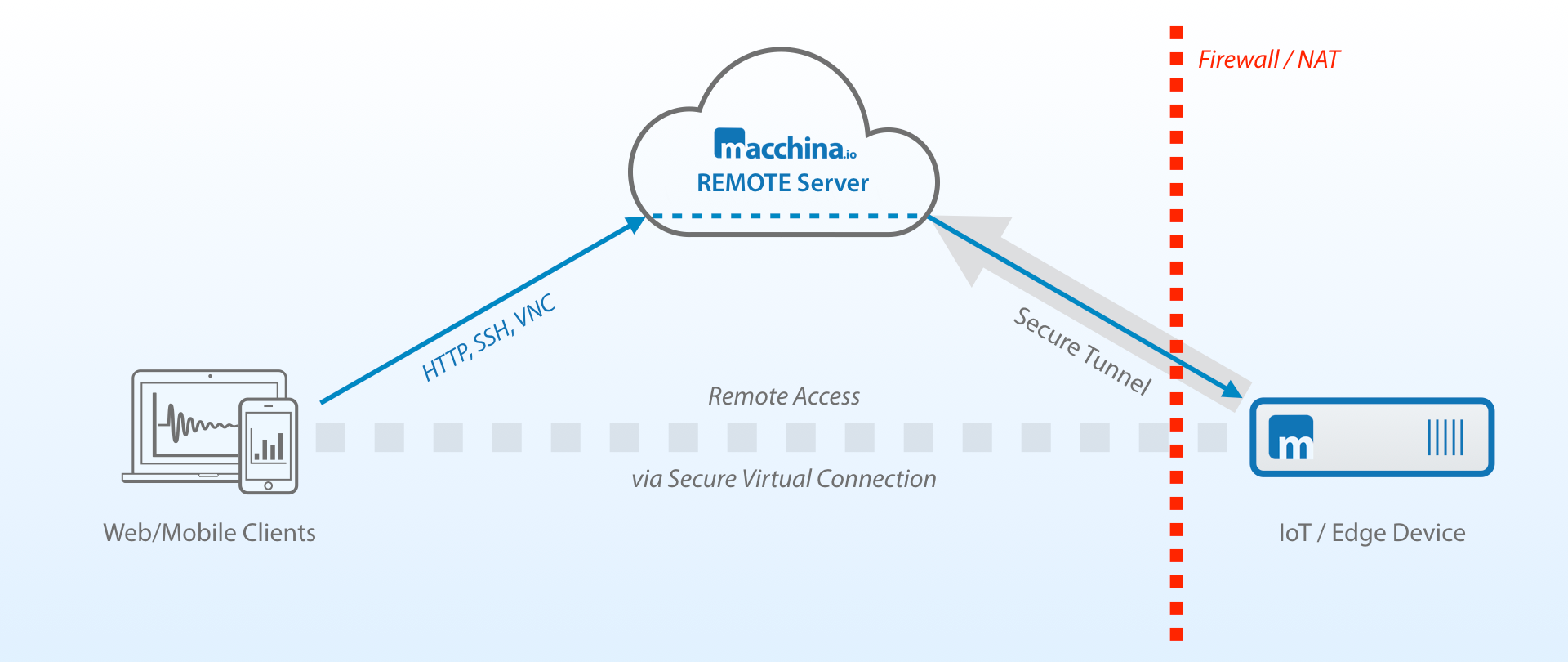
Another key consideration is the choice of tools and technologies. While there are numerous solutions available, some are more effective than others in simplifying the process and providing the necessary security. For instance, the use of SSH (Secure Shell) is a common method for remote access, particularly for devices running Linux-based operating systems. SSH provides a secure channel for communication, allowing you to manage and control your devices remotely. However, to use SSH effectively behind firewalls, you often need to employ techniques like port forwarding or reverse proxying, which can add complexity to the setup process.
Furthermore, the availability of a robust offline installer can be crucial for environments where internet connectivity is unreliable or unavailable during the initial setup. An offline installer allows you to install and configure the necessary software on your devices without requiring an active internet connection, streamlining the deployment process. This is especially important for industrial settings or remote locations where reliable internet access cannot be guaranteed. This ensures the seamless functionality of the tools, and the system runs as desired.
This guide is not just another tech tutorial; it's a comprehensive resource designed to equip you with the knowledge and practical steps to make remote IoT access a reality. Whether you're a seasoned IT professional or a curious enthusiast, this guide provides clear, concise instructions and valuable insights to help you navigate the complexities of remote access and create a secure and efficient IoT ecosystem.
Let's be honest, setting up remote access for IoT devices can feel like solving a puzzle. The various components, from firewalls and routers to security protocols and connection methods, can seem daunting. However, with the right tools and knowledge, the process becomes a breeze. This article will break down the process into manageable steps, providing clear instructions and practical examples to help you establish secure and reliable remote connections to your IoT devices. We'll cover everything from the basics of setting up SSH servers to advanced techniques for bypassing firewalls and securing your network.
By following the steps outlined in this article, you can establish secure connections, implement best practices for security, and troubleshoot common issues effectively. You will gain a thorough understanding of how to effectively use remoteiot behind firewalls on Windows systems, empowering you to manage your IoT devices with confidence and efficiency. This includes everything from installing and configuring an SSH server on your Linux-based IoT device to setting up a secure reverse proxy connection. This approach will help you avoid the need for port forwarding and complex VPN configurations, making your remote access setup simpler and more reliable.
The focus on security is paramount. We will delve into the critical aspects of securing your IoT devices for remote access, including changing default credentials, enabling firewall rules, and using robust encryption. We will also discuss the importance of using a VPN connection, which can provide an extra layer of security by creating a secure tunnel for all your communications. Understanding and implementing these security measures is crucial to protecting your devices and your data from unauthorized access.
Beyond the technical aspects, this guide will also explore the practical benefits of remote IoT access. You'll learn how to control remote Raspberry Pi devices from anywhere, manage and monitor your IoT devices, set cloud alerts, and even run batch jobs remotely. This increased functionality will dramatically enhance your productivity and allow you to manage your devices more efficiently. With remote access, you can stay in control, even when you're not physically present.
The guide will also provide a clear understanding of what IoT remote access is. It's the ability to connect to, monitor, and control your IoT devices from a remote location. This capability is critical for managing and supporting a wide array of IoT devices, such as smart appliances, industrial sensors, and connected vehicles. This understanding will empower you to make informed decisions about your IoT infrastructure and how to manage it effectively.
To make the process easier, we will guide you through installing, configuring, and enabling an SSH server on your Linux-based IoT device. We will also explore how to install and set up a solution that creates an SSL/TLS-based reverse proxy connection to your SSH server. This innovative approach eliminates the need for complex network configurations and makes the entire process more straightforward. By following these steps, you will have a secure and reliable remote access solution in no time.
We will also address the common challenges of remote access, such as dealing with firewalls and restricted networks. You'll learn how to configure your devices to bypass these obstacles, allowing you to establish a secure connection to your IoT devices, regardless of their location or network configuration. These strategies will help you to effectively manage your devices and to access your device from any location.
This comprehensive guide will not only teach you the technical aspects of remote IoT access but also provide you with the confidence to manage your devices effectively. You will gain the knowledge to troubleshoot common issues and to implement best practices for security and efficiency. The goal is to empower you to take control of your IoT ecosystem, regardless of the complexity.
By focusing on practical steps and real-world scenarios, this guide ensures that you are equipped with the skills and knowledge to implement successful remote access solutions for your IoT devices. This will allow you to experience the full benefits of remote access, including enhanced control, improved efficiency, and increased productivity. Its time to unlock the potential of your IoT devices, and this guide will show you how.
What is IoT remote access? It's the ability to connect to, monitor, and control your IoT devices from a remote location. This critical function is the cornerstone of efficient IoT management, enabling you to manage and support a diverse range of IoT devices without requiring a physical presence. This is vital for everything from smart appliances and industrial sensors to connected vehicles, streamlining operations and increasing responsiveness.
Understanding the basics of IoT and remote access is the first step. IoT, the Internet of Things, refers to the network of physical objects embedded with sensors, software, and connectivity that allows them to exchange data with other devices and systems. Remote access allows you to interact with these devices from a distance, enabling you to monitor their status, control their functions, and receive alerts, all without needing to be physically present.
To ensure secure IoT remote device access, all network traffic should use robust encryption such as TLS or DTLS. Properly configure firewalls to allow only the necessary traffic, and consider using a VPN connection for remote access to the IoT network. These measures create a secure environment, safeguarding your devices and their data from unauthorized access. Implementing these practices will minimize the potential for data breaches and ensure the confidentiality of your IoT data.
The right tools are essential for seamless functionality. This includes robust offline installers to overcome connectivity challenges, secure methods like SSH for establishing remote connections, and comprehensive management platforms for controlling and monitoring your devices. By choosing the right tools, you simplify the process and minimize potential issues, optimizing the performance of your IoT ecosystem.
Securing IoT devices for remote access is paramount. Start by changing default passwords and usernames to protect against unauthorized access. Enable firewall rules to restrict access to specific IP addresses, limiting the potential attack surface. These initial steps help you build a strong foundation of security.
When setting up IoT devices for SSH (Secure Shell), it's crucial to implement these security measures to protect against unauthorized access. SSH provides a secure method of accessing your devices remotely, and by implementing best security practices, you can create a robust and secure setup.
Iot remote access offers users the ability to control and monitor devices from virtually anywhere, enhancing productivity and convenience. This level of access is particularly valuable for troubleshooting, device management, and real-time data monitoring.
However, ensuring seamless functionality requires the right tools, including a robust offline installer. Having an offline installer allows you to configure your devices, regardless of network conditions, making the initial setup process more reliable and less dependent on internet availability.