SSH In IoT: Secure Remote Access & Data Protection Explained
Is your digital frontier truly fortified against the ever-present threats of the Internet of Things (IoT)? Secure Shell (SSH) is not merely a technical protocol; it's a critical cornerstone in the architecture of secure IoT communications, offering a robust defense against cyber intrusions.
The world, increasingly interwoven with interconnected devices, presents a complex tapestry of vulnerabilities. From smart home appliances to industrial control systems, the IoT landscape has expanded exponentially. This growth, however, has created a fertile ground for malicious actors, with the potential for catastrophic breaches ranging from data theft to operational disruption. Therefore, the understanding and effective implementation of security protocols, such as SSH, is not an option, it's a necessity.
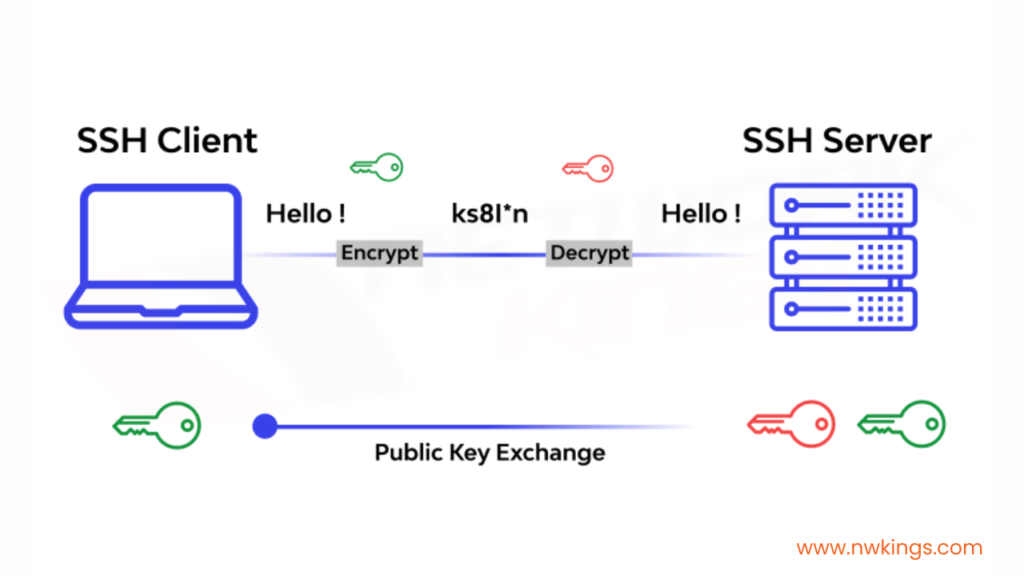
SSH, in its essence, is a cryptographic network protocol. It is designed to establish secure communication channels over insecure networks. SSH provides encrypted data transfer, remote command execution, and secure access to various network services.
The genesis of SSH was focused on secure remote login and file transfer. In the modern era of IoT, the protocol has morphed into an indispensable tool in securing data transfer, device management, and overall network integrity. Its role has become even more pronounced.
One of the primary functions of SSH is to create an encrypted tunnel between IoT devices and their management systems. This is essential to provide the privacy of data transmitted between devices. It protects sensitive information from being intercepted and exploited by unauthorized parties. In the context of IoT, where data is constantly being exchanged, this aspect of SSH is of paramount importance.
SSH, also known as Secure Shell, is a cryptographic network protocol. It is designed to secure data communication over networks.
This protocol goes beyond just confidentiality; it facilitates remote command execution, allowing administrators to manage and control devices remotely. This is important for software updates, configuration changes, and overall system administration. SSH provides remote access to devices. This streamlines maintenance tasks and allows for prompt responses to any device issues.
The Secure Shell, is a powerful tool. It provides strong encryption. It provides integrity protection. The use of SSH in an IoT infrastructure also significantly reduces the risk of unauthorized access to the network and its connected devices. In a landscape rife with sophisticated attacks, SSH acts as the first line of defense.
The role of SSH in the IoT ecosystem is increasingly important, as connected devices continue to proliferate. From smart homes to industrial applications, the need to protect sensitive information and ensure secure communication is paramount. The potential impact of compromised IoT devices, ranging from data breaches to physical harm, is extensive. Understanding SSH, and its proper configuration, will play a pivotal role in managing and mitigating these risks.
Despite challenges, the benefits of SSH far outweigh the potential drawbacks. With the right expertise and implementation strategy, the difficulties can be effectively addressed, offering a robust and secure communication framework for IoT devices.
The need to protect interconnected devices from cyber threats is becoming ever-more critical, understanding the roles of SSH is vital. Best practices are a very important part of maximizing security. SSH provides remote access to devices, keeping data confidential and people safe.
SSH's function is to act as a strong encryption layer. Once the connection is established between the SSH client and server, the data is encrypted using parameters that were exchanged during setup.
Secure Shell, known as SSH, provides a secure communication channel. This enables encrypted data transfer and remote access to IoT devices. Secure file transfers over SSH allow access to all shell accounts on a remote SFTP server.
The importance of SSH cannot be understated in the complex IoT environment. It is a fundamental component. It acts as a shield, defending against malicious attacks, and ensuring data integrity. To effectively secure your IoT infrastructure, it is imperative to explore the capabilities of SSH and implement best practices for its usage.
The Secure Shell (SSH) is a network protocol that provides secure remote access over an insecure network. The secure shell is a replacement for telnet, rsh, and rlogin.
Here is a table detailing the key aspects of SSH in the context of the Internet of Things:
| Aspect | Description | Importance in IoT | Benefits | Potential Challenges |
|---|---|---|---|---|
| Definition | A cryptographic network protocol providing secure communication channels over insecure networks. | Essential for protecting sensitive data transmitted between IoT devices. | Secure data transfer, remote access, and command execution. | Configuration complexity, key management, and resource constraints on devices. |
| Functionality | Encrypts data, enables remote access, and allows for secure file transfer. | Ensures confidentiality, integrity, and authentication of data exchanged. | Protects data from interception, provides secure remote management, and enables secure software updates. | Requires proper setup and security configurations to avoid vulnerabilities. |
| Security | Uses encryption algorithms (e.g., AES, RSA) to protect data. | Critical for defending against cyber threats and ensuring data privacy. | Reduces the risk of unauthorized access, protects against eavesdropping, and prevents data tampering. | Requires up-to-date security practices and constant monitoring to maintain strong security. |
| Implementation | Implemented on both IoT devices and managing systems. | Requires careful planning to ensure all devices are properly secured. | Allows for scalable management and monitoring of IoT devices. | Requires expertise to configure, secure, and maintain SSH implementation across different devices. |
| Use Cases | Remote device management, secure file transfer, and secure command execution. | Critical for maintaining and securing IoT devices. | Enables remote troubleshooting, secure software updates, and remote configuration changes. | May not be suitable for all IoT devices due to resource constraints. |
One of the most important applications of SSH within the IoT world involves secure remote access to devices. This capability is extremely valuable to IT administrators and security personnel. It allows for remote troubleshooting, software updates, and configuration changes.
The benefits of using SSH in IoT are manifold. It ensures the confidentiality of the data. It provides strong encryption. The remote access capability streamlines device management, reducing the need for on-site interventions. It also supports the integrity of data, preventing any kind of tampering. Using SSH, IoT remote access is safe, easy to deploy, and dependable.
Best practices for using SSH in IoT maximizing security with SSH. With the right tools and expertise, you can implement SSH successfully. The use of SSH is to securely supervise IoT networks, keeping data confidential and people safe.
The full form of SFTP is SSH File Transfer Protocol, which is part of the SSH protocol suite, SFTP provides secure file transfers over SSH. Learn how to set up, secure, and configure SSH for remote access with our detailed guide.
IoT breaches, which are all too common, are a harsh reminder of the importance of robust security measures. The 'Mirai' attacks are a case in point, where millions of devices were compromised, resulting in distributed denial-of-service (DDoS) attacks. The ability to remotely access and control devices allows the attackers to disrupt services, steal data, and cause widespread havoc. Protecting your IoT network from such attacks is the ultimate goal of SSH implementation.
One particularly powerful tool in this realm is SSH. It provides secure remote access over an insecure network. Cisco is a worldwide technology leader.
In conclusion, SSH stands as a cornerstone in IoT security. It serves as a vital tool for protecting the data transmitted between devices, facilitating remote access. Its implementation is not only beneficial; it is critical to create a secure, and reliable environment. Proper setup, security configuration, and continuous monitoring are key components to leverage the full potential of SSH, fortifying your IoT infrastructure against the challenges of the modern digital landscape.
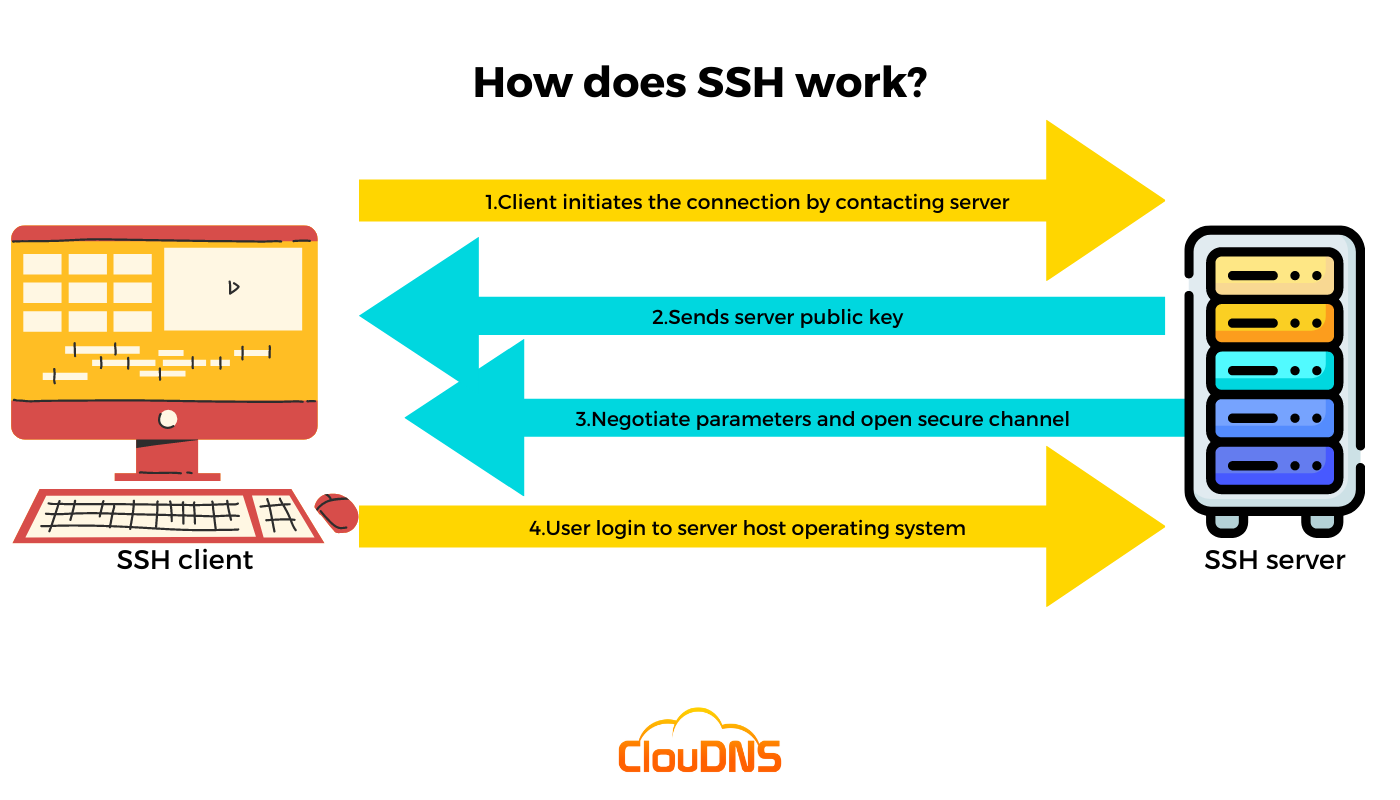
.png)