SSH Key Management: Best Practices For Security & Control
Are you concerned about the security of your remote access and IT infrastructure? Properly managing SSH keys is not just a best practice; it's a critical necessity for safeguarding your digital assets and ensuring business continuity.
In the digital age, secure remote access is paramount. The Secure Shell (SSH) protocol provides a vital means of accessing servers and databases remotely. It also allows secure data transmission over networks. However, the very convenience of SSH introduces significant security challenges. This article delves into the critical aspects of SSH key management, offering a comprehensive guide to understanding, implementing, and maintaining robust security protocols within your IT environment.
Let's break down the core of SSH key management. It is essentially the practice of managing those critical admin keys so that you know at all times:
- Who has access?
- What systems they can access?
- When their access is valid?
SSH keys offer a significantly enhanced security posture compared to traditional password-based authentication. They provide an essential safeguard for access to servers and encrypt data transmission over networks. However, they also introduce a complex management challenge. Without careful planning, the benefits of using SSH keys can quickly be negated, leaving your systems vulnerable to attack.
This guide is designed to give you a clear picture of what to focus on, whether you're looking to implement SSH key management practices or trying to fine-tune your existing system.
Here's a table outlining the key areas that this guide will explore:
| Area | Description |
|---|---|
| Key Generation | Best practices for generating strong, secure SSH key pairs. |
| Key Protection | Strategies for safeguarding your private keys from unauthorized access. |
| Key Rotation | The importance of regularly rotating keys to mitigate risk. |
| Backup and Recovery | Developing effective backup and recovery plans for your keys. |
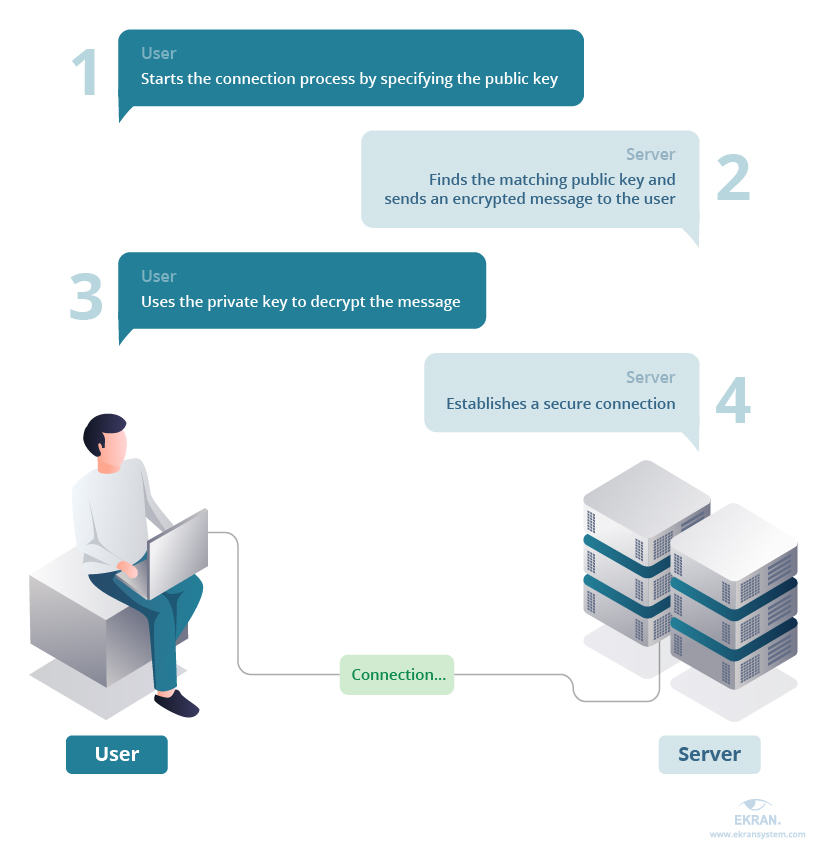
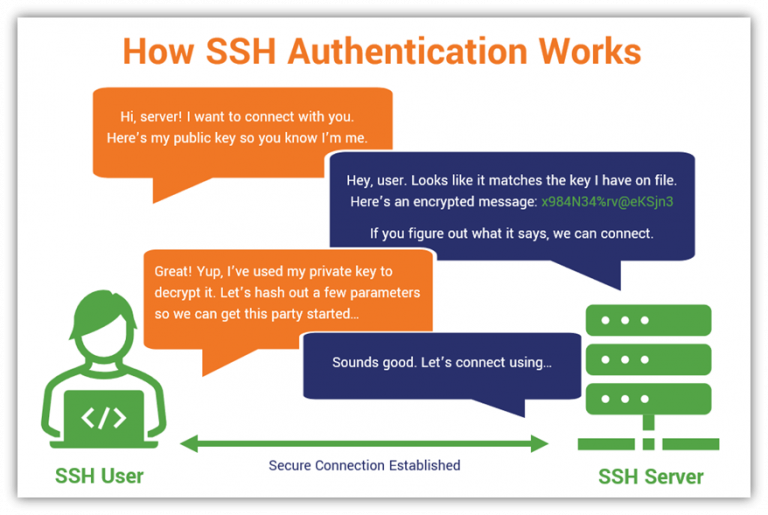
SSH keys, when used correctly, are a cornerstone of secure remote access. They work by using a pair of cryptographic keys: a public key and a private key. The public key is installed on the remote server, while the private key is kept securely on the user's machine. When a user attempts to connect to the server, the server uses the public key to verify the user's identity. If the private key matches the public key, access is granted. This process is far more secure than passwords, as it eliminates the need to transmit a password over the network.
While the process seems simple, complexities abound in real-world environments. Proper planning is required. The potential risks include: unauthorized access due to compromised keys, inefficient management of large numbers of keys, and difficulty in auditing access. Moreover, compliance requirements may necessitate specific key management practices, adding another layer of complexity.
Here is a list of 14 SSH key management best practices:
- Generate Strong Keys: Employ robust key generation algorithms such as RSA or Ed25519 with sufficient key lengths (e.g., 4096 bits for RSA) to resist brute-force attacks.
- Protect Private Keys: Securely store private keys. Implement strong access controls, encryption, and consider using hardware security modules (HSMs) or smart cards.
- Implement Key Rotation: Regularly rotate SSH keys, ideally every 90 days or less, to limit the impact of a compromised key.
- Centralized Key Management: Use a centralized key management system to track, manage, and audit all keys.
- Automate Key Lifecycle: Automate key requests, rollouts, rotations, and removals to streamline processes and minimize manual errors.
- Use Key-Based Authentication: Avoid password-based authentication in favor of SSH key authentication for enhanced security.
- Disable Password Authentication: Disable password authentication on servers where possible to reduce the attack surface.
- Monitor Key Usage: Regularly monitor SSH key usage for any suspicious activity or unauthorized access attempts.
- Implement Access Controls: Define and enforce strict access controls based on the principle of least privilege.
- Regular Audits: Conduct regular audits of SSH key configurations and usage to identify potential vulnerabilities.
- Backup and Recovery: Establish a reliable backup and recovery plan for SSH keys to ensure business continuity.
- Educate Users: Train users on secure key management practices, including the importance of protecting private keys and reporting suspicious activity.
- Consider Hardware Security Modules (HSMs): Use HSMs for storing and managing critical keys, enhancing security and control.
- Keep Software Updated: Keep SSH software and related tools up to date to patch known vulnerabilities.
These best practices can be divided into four overarching categories:
- Key Generation and Configuration: focus on creating secure keys and configuring SSH properly.
- Key Storage and Protection: this focuses on protecting and securing your private keys.
- Key Lifecycle Management: The policies and processes for managing your keys from creation to deletion.
- Monitoring and Auditing: this involves constant monitoring of your environment, in order to ensure a high degree of security.
With the vast numbers of SSH keys that enterprises have today, manual processes are infeasible. Automation can help significantly lower the overhead and risk of manual key lifecycle management. Automating key requests, roll outs, rotations, and removals can streamline processes and minimize manual errors. Fully automate ssh key lifecycle processes, including key requests, roll outs, rotations, and removal. Most importantly, automation can significantly improve security, efficiency, and availability.
Organizations must not ignore the risks and vulnerabilities introduced due to the lack of security around the management of SSH keys. You can ensure proper protection of keys with ssh key management a combination of practices, policies, and tools for establishing secure ssh key usage routines within an organization. SSH key management can significantly enhance corporate cybersecurity by protecting networks and systems from both external and insider attacks.
To help you visualize the key management process and how these recommendations come together, consider a simplified workflow:
- Key Creation: An authorized user requests a new SSH key pair through a secure process.
- Storage: The private key is generated and stored securely, possibly within an HSM or encrypted vault.
- Deployment: The public key is deployed to the designated server, often through automated tools.
- Use: The user authenticates using the private key, gaining access to the server.
- Rotation: After a predefined period, the key is automatically rotated and a new key is generated. The old keys can be safely revoked.
- Revocation: If a key is compromised or a user's access needs to be revoked, it is removed from the authorized_keys file.
By adopting these practices, you can drastically reduce the risk of unauthorized access and safeguard your IT infrastructure. Moreover, it is crucial to stay informed and adaptable. The security landscape is ever-changing, and new threats emerge regularly. Keep up-to-date on the latest vulnerabilities and adjust your key management strategy accordingly. Continuously assess your security posture and update your policies and tools to stay ahead of potential threats. For more detailed information, you can refer to the following resources:
OWASP Top Ten. This will help with understanding the different aspects of secure SSH key management in depth.