Remote SSH Access To IoT Devices: A Beginner's Guide
In an era defined by interconnected devices, how can one securely and efficiently manage those devices that are geographically distant? The answer lies in understanding and mastering the art of remote access, particularly the use of Secure Shell (SSH) to manage Internet of Things (IoT) devices across the internet.
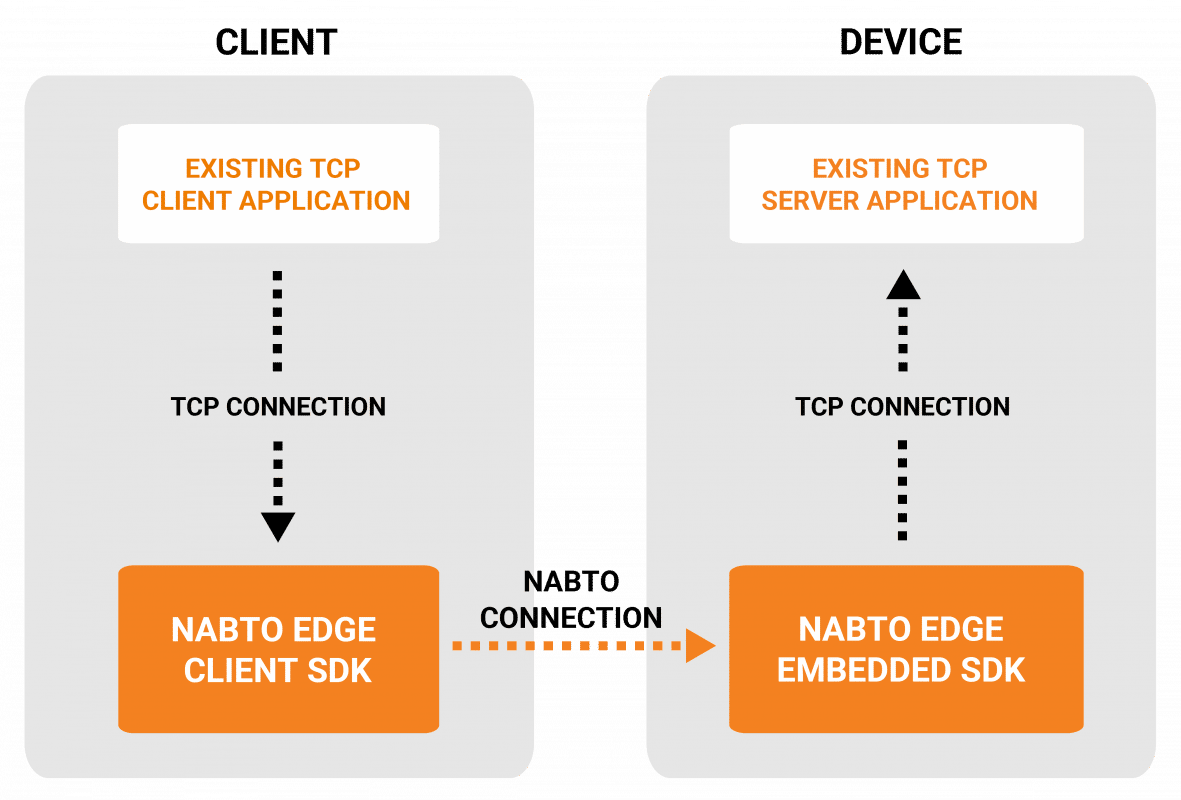
The challenge often arises when these devices reside behind firewalls, impenetrable barriers that prevent direct access. You can't simply initiate an SSH session into the device because the firewall, a crucial security measure, actively blocks all inbound traffic. Traditional methods of accessing remote devices falter, leaving many tech enthusiasts and developers searching for viable solutions. This situation necessitates a clever strategy, a workaround that allows you to traverse these digital obstacles and reach the device. The tutorials guide one through the steps of opening a tunnel. The process involves establishing a secure pathway that can act as a bridge to communicate with these remote devices.
| Aspect | Details |
|---|---|
| Core Technology | Secure Shell (SSH) |
| Purpose | Remote Access and Management of IoT Devices |
| Challenge | Overcoming Firewalls and Inbound Traffic Restrictions |
| Solution | Creating Tunnels for Secure Communication |
| Benefits | Enables Sending Commands, Transferring Files, and Troubleshooting Remotely |
| Alternative Communication | VPN or Proxy connection |
| Prerequisites | Enable SSH on the IoT device |
| Essential Element | Obtain the IoT device IP Address |
| Client Examples | Terminal on Linux or MacOS, PuTTY on Windows |
The concept of remote access might seem straightforward, but the execution requires a deep understanding of the underlying technologies. This is where Secure Shell (SSH) comes into play, transforming into an essential tool for developers and tech enthusiasts alike. SSH provides a secure, encrypted connection that allows you to not only access a remote device but also manage and troubleshoot it as if you were sitting right in front of it.
The magic of remote connecting IoT devices over the internet using ssh is becoming increasingly relevant as the Internet of Things (IoT) landscape continues its exponential growth. This includes the secure management of IoT devices. Whether you're a tech enthusiast, a developer, or someone curious about the world of IoT, the following steps will provide the foundation needed to create the necessary connections. You have an IoT device agent running on the remote device that connects to the AWS IoT Device Gateway and is configured with an MQTT topic subscription. For more information, see connect a device to the AWS IoT Device Gateway. AWS offers a range of IoT offerings, but people not using AWS can take a more traditional approach of using ssh with a VPN or proxy connection. This provides a communication layer for devices to connect to the internet and interact with AWS services. The significance of SSH lies in its ability to create a secure, encrypted tunnel between your computer and a remote device. This 'tunnel' allows you to transmit commands, transfer files, and even troubleshoot issues, all without physically being present at the device's location.
To initiate remote access, ensuring that the SSH service is up and running on the target device is critical. After this service is active, a connection can be tested from a remote computer to confirm operability. This is a foundational step, as it verifies the device is ready to accept and respond to SSH requests.
Imagine needing to access a device that's behind a firewall. You can't start a direct SSH session into the device because the firewall blocks all inbound traffic. That's where the concepts of tunneling come in. One could open a tunnel to start an SSH session to a remote device, this way one can start an SSH connection to the device by turning on SSH on that device. Endpoints and ports need to be able to perform outbound requests to specific endpoints and ports. This allows for the basic operation of a device.
Before diving into the process, a few essential prerequisites must be met. Ensuring that SSH is enabled on your IoT device is non-negotiable, as this is the fundamental requirement for any SSH connection. Next, obtaining the IoT device's IP address is crucial; this IP address is the unique identifier that will allow you to locate and connect to the device. Once enabled, you can connect to your device using an SSH client like PuTTY or directly from your terminal.
Once all the necessary preparations have been completed, establishing an SSH connection with your IoT device becomes a straightforward process. Lets go through the steps. First, open your preferred SSH client on your computer. This could be the terminal on Linux or macOS, PuTTY on Windows, or another client that suits your preferences. Next, use the SSH command followed by the username and IP address of the device. For example, `ssh user@192.168.1.100` will initiate a connection to the device with the IP address 192.168.1.100. Upon executing this command, youll be prompted to authenticate with the device, usually by entering the password associated with the specified username. Successfully authenticating will grant you access to the device's command line, allowing you to send commands, transfer files, and troubleshoot issues.
The importance of SSH in the realm of IoT cannot be overstated. As the Internet of Things (IoT) continues to expand, understanding SSH IoT device examples is crucial for maintaining robust cybersecurity and ensuring seamless device communication. SSH provides a secure conduit for accessing and managing remote devices, making it an indispensable tool for developers and tech enthusiasts alike. It's basically a protocol that lets you access and manage remote devices securely. Think of it as a secure tunnel between your computer and an IoT device, allowing you to send commands, transfer files, and troubleshoot issues without being physically present.
With the SSH server configured, you can now connect to your IoT device from the SSH client. This is where you'll use the SSH command, followed by the username and IP address of the device. For example, `ssh user@192.168.1.100` will initiate a connection to the device with the IP address 192.168.1.100. The process involves establishing a secure pathway that can act as a bridge to communicate with these remote devices. The practical examples of using SSH with IoT devices often involve the use of a VPN or proxy connection for added security and to bypass any potential firewall restrictions. This provides a communication layer for devices to connect to the internet and interact with services.