Secure Remote IoT P2P: Guide & Solutions - [We Did Not Find...]
Is the promise of seamless connectivity and remote control within the Internet of Things (IoT) truly within our grasp? The answer, especially when focusing on secure peer-to-peer (P2P) communication, lies in a blend of robust protocols and a thoughtful approach to implementation, particularly with devices like the Raspberry Pi. The initial search results, unfortunately, didn't yield the direct answers we were hoping for, but the core concepts remain compelling, and they deserve a closer look.
The landscape of IoT is vast and ever-expanding. From smart homes to industrial automation, the ability to remotely monitor and control devices is rapidly becoming a necessity. Consider the Arduino IoT Remote Phone Application, a tool that empowers users to interact with their dashboards within the Arduino Cloud. This application further extends its capabilities by offering access to your phone's internal sensors. With the application, you can access GPS data, light sensors, and IMU (Inertial Measurement Unit) data, depending on your specific mobile phone model. This two-way interaction underscores the dynamic potential of IoT, where data flows seamlessly between the physical world and our digital interfaces.
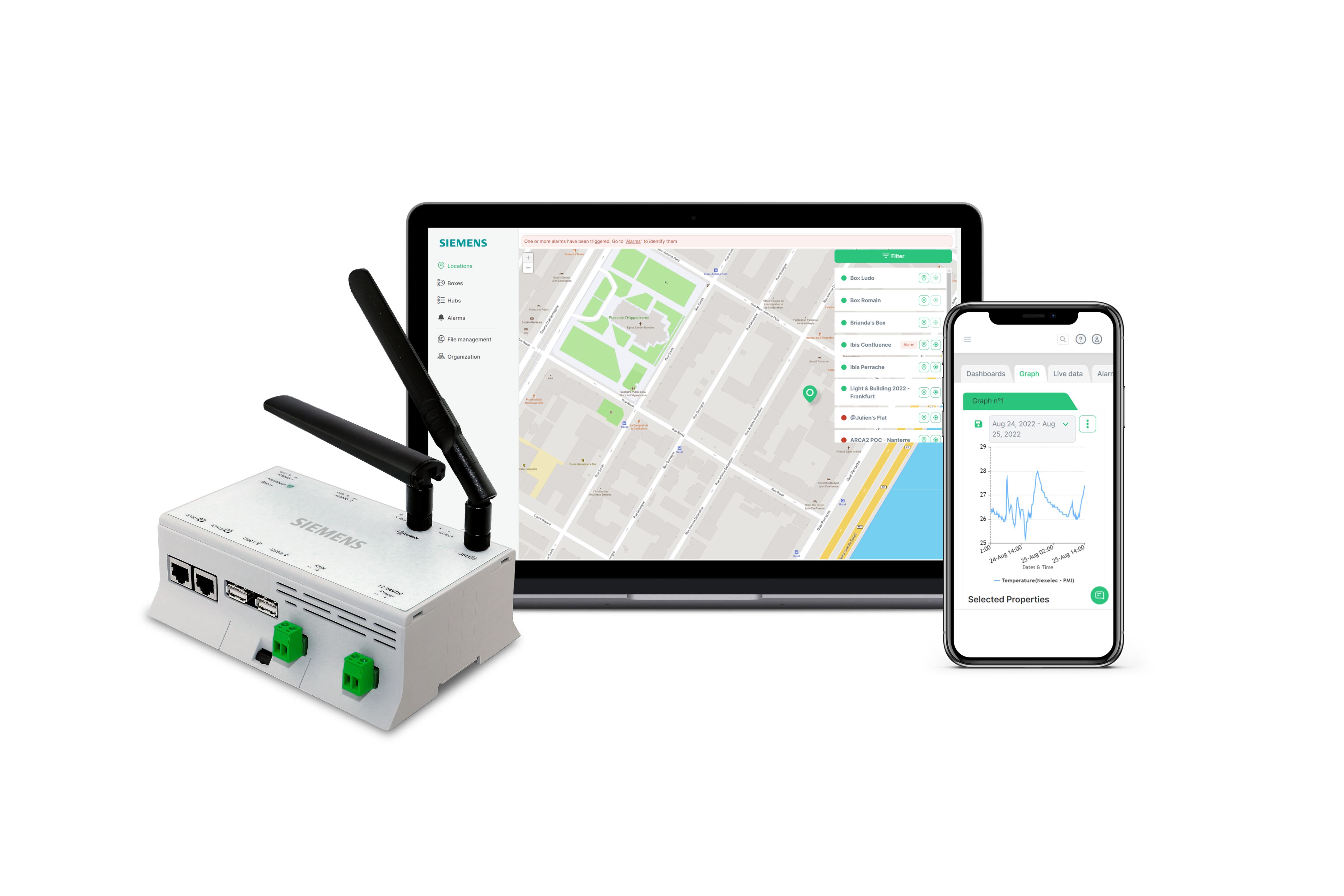
Let's delve into the technical underpinnings. If you're using a Raspberry Pi, one of the most popular platforms in the IoT realm, a common approach involves establishing a secure connection. For those looking for a practical, accessible solution, the key is often the remoteiot service.
To get started, one of the initial steps is to install the remoteiot service. This typically involves accessing the Raspberry Pi's terminal, either directly or through a secure shell (SSH) connection on your local network. Once the service is installed, the next phase is to open the remoteiot portal in your preferred web browser and login to the dashboard. Success is confirmed when your Raspberry Pi appears in the list of account devices, signaling the establishment of a functional communication link.
Beyond these introductory steps, several critical aspects should be considered when approaching remote IoT P2P. Securely connecting these devices and ensuring the privacy and integrity of data transmission is paramount. This involves implementing a secure P2P connection, a focus that guides the next series of points.
As the digital world grows, the Internet of Things (IoT) is booming, and Raspberry Pi is leading the race. Its design concentrates on adaptability, independence, and reliability. A single connectivity device can interact with thousands of sensors, offering many possibilities. Equipped with greater computational power than a sensor, they can also be managed remotely over the internet. This offers an extraordinary potential in various fields.
Let's consider an example, logistics and supply chain management. Remote IoT monitoring offers a significant advantage by providing visibility into the movement of goods and resources. This visibility results in optimized delivery routes, efficient resource allocation, and overall cost savings. It's just one example of the widespread benefits of secure IoT connectivity.
The AWS platform provides a set of options for IoT, however, those not using AWS can use the more traditional approach using SSH with a VPN or proxy connection. This creates a communication layer for devices to connect to the internet and interact with various services. Setting up a secure peer-to-peer (P2P) connection requires a series of steps that should be followed carefully to ensure maximum security.
The central topic becomes how to securely connect remote IoT P2P devices. It is a key focus of the entire process and is a matter of security and data transfer. These steps involve several key steps to implement the P2P connection and ensure that everything is working efficiently.
One of the first things to do is to select a P2P protocol that prioritizes security. This can include protocols like WebRTC or UPnP. WebRTC allows for the establishment of direct connections, providing better performance. The process demands a thorough strategy that considers security and functionality.
If you are looking to securely connect remote IoT P2P Raspberry Pi devices, you are in the right place. These devices, when correctly configured, offer a powerful platform for realizing the benefits of remote connectivity, data collection, and control.
The Raspberry Pi has emerged as a cornerstone of IoT development, a testament to its affordability, versatility, and ease of use. Its popularity has fuelled the growth of innovative applications across various sectors. Because of this versatility, there are many different ways to use the Raspberry Pi in conjunction with the IoT.
The design of a Raspberry Pi focuses on providing a reliable, autonomous, and adaptable solution for a range of applications. Its adaptability lets the system interact with thousands of sensors. It's a powerful device that can handle a wide variety of tasks and can be remotely controlled via the internet.
Looking deeper into the possibilities, there is a real potential for the creation of many new IoT systems by using Raspberry Pi technology. This includes the ability to monitor and control sensors in remote environments. These systems have the potential to change the way we interact with the world.
We're seeing significant advancements in diverse sectors. For example, in supply chain management, remote IoT monitoring offers a significant advantage. By keeping track of goods and resources, companies can fine-tune delivery routes and allocate resources efficiently. This results in considerable cost savings and greater operational effectiveness.
When looking for answers, be sure to double-check your search queries. Using precise keywords will greatly increase your chances of finding useful information about securely connecting remote IoT P2P devices.
This technological world can sometimes be complicated and challenging to grasp. By following this framework, you will be able to navigate this digital revolution with confidence.