Access RemoteIoT On Mac: Behind A Firewall & Securely
Are you finding it challenging to maintain consistent access to your IoT devices when your Mac is behind a firewall? Navigating the complexities of remoteiot access while adhering to robust security protocols is not just a technical exercise; it's a critical necessity in today's interconnected world.
This guide is meticulously designed to provide a deep dive into the setup and management of remoteiot, specifically when operating behind a firewall on a Mac. The goal is to equip you with the knowledge and techniques necessary to achieve seamless connectivity, regardless of the network restrictions you face.
Understanding how to effectively manage remoteiot access through a firewall is paramount. Let's explore the crucial aspects that will help you maintain robust security and efficient performance.
Many users encounter hurdles when trying to establish a secure connection to their remoteiot devices from a Mac that is protected by a firewall. This often involves complex configurations and a solid understanding of network protocols. This guide simplifies the process, offering actionable steps that will enable you to unlock the full potential of remoteiot without sacrificing the security of your system. We will address the most common challenges, offering clear and concise solutions.
Using remoteiot behind a firewall with a Mac server represents a powerful solution, allowing for secure and efficient management of IoT devices. This setup provides the flexibility to control and monitor devices from anywhere, even when those devices are behind a network's security perimeter. This method is particularly beneficial for professionals managing a fleet of IoT devices, offering centralized control and robust security features.
By the end of this comprehensive guide, you will have gained a comprehensive understanding of remoteiot, its functionalities, and how to securely configure it on your Mac, even when operating behind a restrictive firewall. The following sections will break down the essential steps and considerations, ensuring that you have the necessary tools to implement a successful and secure remoteiot configuration. This approach will cover everything from basic setup to advanced security measures, providing a complete toolkit for secure remote access.
The core of this discussion is about empowering users to overcome the limitations imposed by firewalls. The primary aim is to help establish secure and reliable connections to IoT devices, no matter where you are located. You'll learn to configure your Mac and firewall settings properly to maintain optimal security. The article offers in-depth explanations of the key methods, including port forwarding, SSH tunneling, and secure connection protocols. These are fundamental for creating a secure and efficient system, enabling access without compromising security.
Let's break down this approach for better understanding. The process starts with the core requirement: setting up and utilizing remoteiot on a Mac while behind a firewall. This means dealing with the obstacles a firewall presents, ensuring smooth and secure connectivity. It also involves using network-related protocols, providing more information on how each one contributes to the security and efficiency of your system.
This article is meticulously designed to provide comprehensive insights into setting up and managing remoteiot behind a firewall. It aims to furnish users with a detailed understanding of the configuration steps and best practices, promoting optimal performance and security.
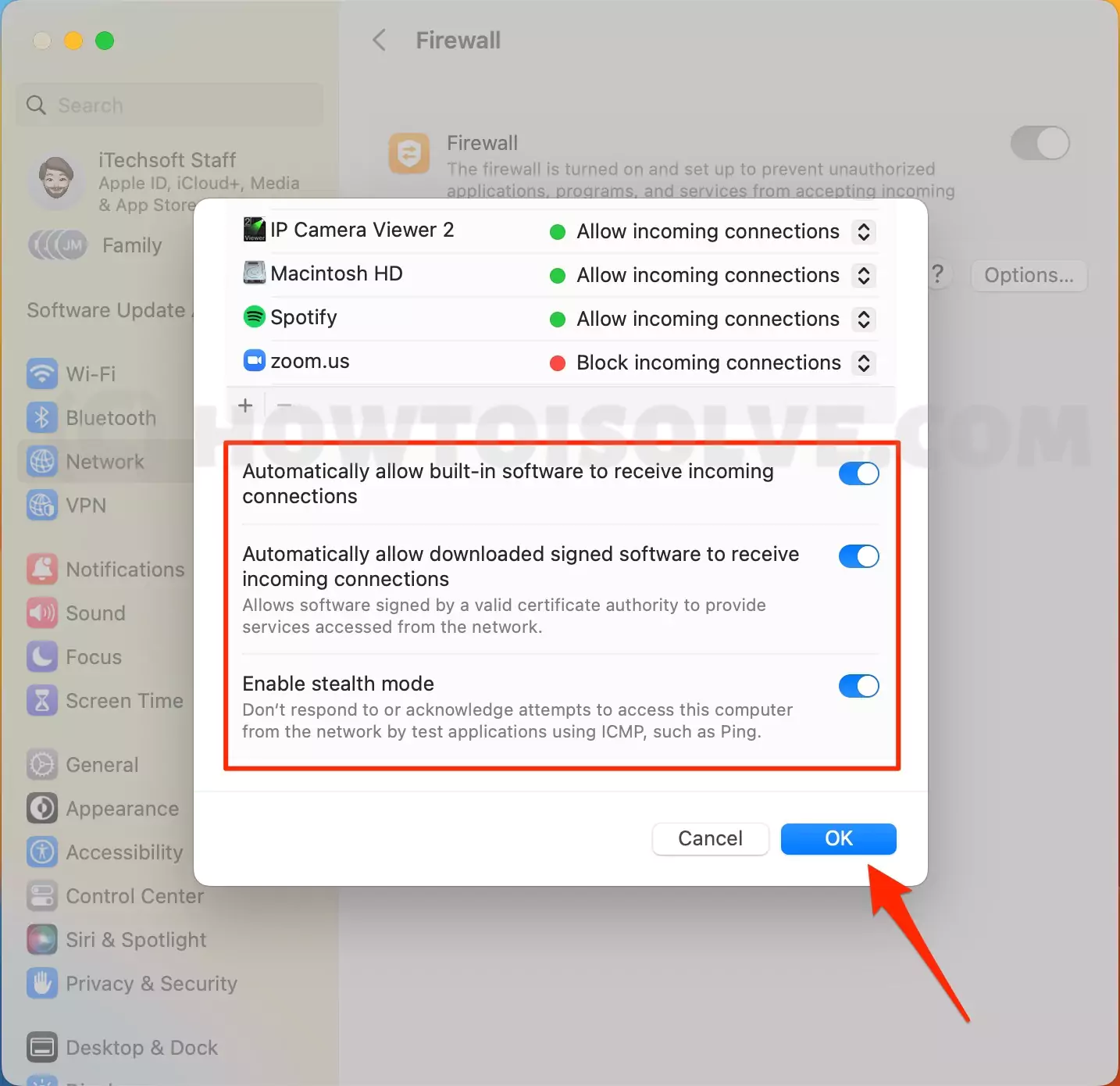
Here is a detailed table outlining the essential steps to configure remoteiot on your Mac to work seamlessly behind a firewall.
| Step | Description | Action | Security Consideration |
|---|---|---|---|
| 1 | Accessing Firewall Settings | Open System Preferences -> Security & Privacy -> Firewall. | Ensure administrative privileges; password required. |
| 2 | Unlocking Firewall Preferences | Click the lock icon in the bottom left corner and enter your password. | Password protection prevents unauthorized changes. |
| 3 | Adding remoteiot to the Firewall | Click the "+" button to add a new app. | Provides the necessary authorization. |
| 4 | Navigating to the remoteiot App | Navigate to the remoteiot app (usually in Applications). Select it. | Ensure you select the correct application file. |
| 5 | Allowing Incoming Connections | Once remoteiot is added to the list, make sure its allowed to receive incoming connections. | Critical for remote access; check the status. |
| 6 | Port Forwarding (if necessary) | Configure your router to forward necessary ports to your Mac's IP address. (e.g., port 22 for SSH, or the port remoteiot uses). | Properly configuring the router is crucial. |
| 7 | SSH Tunneling (if applicable) | Set up an SSH tunnel to securely forward traffic through the firewall. Use `ssh -L [local_port]:[remote_host]:[remote_port] [user]@[server_ip]` | Secures data transmission. |
| 8 | VPN Setup (Alternative) | If your network allows it, setup a VPN connection (e.g., using Tunnelblick or similar) on your Mac. | Provides a secure tunnel. |
| 9 | Testing the Connection | After configuration, test the connection from outside your local network to ensure everything works as expected. | Essential for confirming setup and that everything works as planned. |
This step-by-step guide offers a structured approach to configuring remoteiot. The process is designed to be clear, enabling seamless remote access while ensuring the security of your network.
In the digital age, understanding how to use remote IoT behind a firewall using a Mac server is crucial for seamless connectivity. This functionality enables users to maintain control and access their devices even when they are behind a network security barrier.
Let's simplify this process for you. Imagine that you have full control over your IoT devices, even when theyre tucked safely behind a corporate firewall. This is a game changer, especially for businesses and individuals that need constant remote access to their devices.
Many users face challenges when trying to establish a secure connection to their remoteiot devices from a Mac that is protected by a firewall. This often involves complex configurations and a solid understanding of network protocols. This guide simplifies the process, offering actionable steps that will enable you to unlock the full potential of remoteiot without sacrificing the security of your system. We will address the most common challenges, offering clear and concise solutions.
By learning how to configure your Mac and firewall settings properly, you can unlock the full potential of remoteiot without compromising security. Proper setup is key to a secure and efficient system. This guide will also cover important considerations like port forwarding, SSH tunneling, and secure connection protocols.
For added convenience, here is an overview of the best tools that can be used for accessing remoteiot from your Mac.
| Tool | Description | Use Case |
|---|---|---|
| SSH Clients (e.g., OpenSSH) | Secure Shell clients offer a way to establish secure connections for remote access. | Used for secure terminal access and tunneling. |
| VPN Clients (e.g., Tunnelblick) | Virtual Private Network clients provide a way to create a secure, encrypted connection over the internet. | Best when a secure tunnel is required, encrypting all traffic. |
| Network Monitoring Tools (e.g., Wireshark) | These tools help monitor and analyze network traffic. | Helps with troubleshooting. |
| Remote Desktop Software | Provides graphical remote control of the Mac. | Useful when visual interface is required. |
This is your ultimate guide to mastering the art of using remoteiot behind a firewall on a Mac. It's a critical skill for modern tech enthusiasts and professionals alike. From detailed how-to guides to advanced configurations, you are provided with all the necessary tools to confidently and securely manage your remoteiot devices.
Remoteiot is a powerful tool that allows users to access their devices remotely, regardless of location. With the proper configuration, this can be achieved safely, protecting your devices and your network. The use of tools and methods discussed in this guide is essential to enable secure and efficient device management.
As remote work and IoT applications become more prevalent, the importance of this knowledge increases. Mastering this skill set offers a significant advantage, allowing users to overcome security limitations and access remote devices seamlessly and securely.
Understanding how to configure and operate remoteiot behind a firewall on a Mac is an essential skill in today's digital landscape. The methods outlined ensure smooth and safe connectivity, offering users full control over their devices.
This resource provides the necessary steps to not only understand the technical challenges but also to ensure compliance with security protocols. Remember, the main goal is to equip you with the knowledge to manage remoteiot effectively and securely.