SSH Into IoT Devices: A Guide To Remote Access With AWS
Are you tired of the limitations of on-site device management, the endless trips, and the rising costs associated with troubleshooting and maintaining your IoT devices? The answer lies in the power of secure, remote access through SSH over the internet using AWS, offering a streamlined and cost-effective solution to the challenges of device management.
In the rapidly evolving world of the Internet of Things (IoT), the ability to remotely access and manage your devices is no longer a luxury, but a necessity. Traditional methods of device management, often involving on-site visits by technicians, can be incredibly complex, time-consuming, and expensive. This is where the integration of Secure Shell (SSH) protocol over the internet, facilitated by Amazon Web Services (AWS), steps in to revolutionize the way we interact with and control our IoT devices. This article serves as a comprehensive guide to securely connecting to your IoT devices over the internet using SSH, specifically focusing on Windows and macOS environments. We'll delve into the necessary steps, explore the underlying technologies, and provide practical examples to empower you to take your IoT projects to the next level.
Before we dive into the technical aspects, let's understand the core concept. SSH, or Secure Shell, is a cryptographic network protocol that allows secure communication over an unsecured network. In the context of IoT, SSH provides a secure channel for remote access, enabling you to control your devices remotely. AWS IoT Core, on the other hand, provides the backbone for this secure communication by facilitating secure connections between your IoT devices and the AWS cloud.
This guide is designed to be your companion, ensuring you're not just implementing a solution, but doing it securely and efficiently. We will walk you through the process step-by-step, from the initial setup to the final connection. We will cover the critical aspects, from installing an SSH server on your device to using SSH clients like PuTTY on Windows, and the use of AWS IoT device management features, like Secure Tunneling, to manage your devices over secure connection. By the end of this article, you will possess the knowledge and tools necessary to establish a secure and efficient remote access system for your IoT devices, regardless of their location.
| Aspect | Details |
|---|---|
| Core Technology | Secure Shell (SSH) Protocol over the internet and AWS IoT Core |
| Operating Systems Supported | Windows and macOS |
| Use Case | Remote Access and Management of IoT Devices |
| Key Benefits | Reduced Complexity and Cost of Device Management, Enhanced Control, Increased Flexibility |
| Prerequisites |
|
| AWS Services Involved | AWS IoT Core, AWS IoT Device Management (optional) |
| Recommended Reading | AWS IoT Core - Official Website |
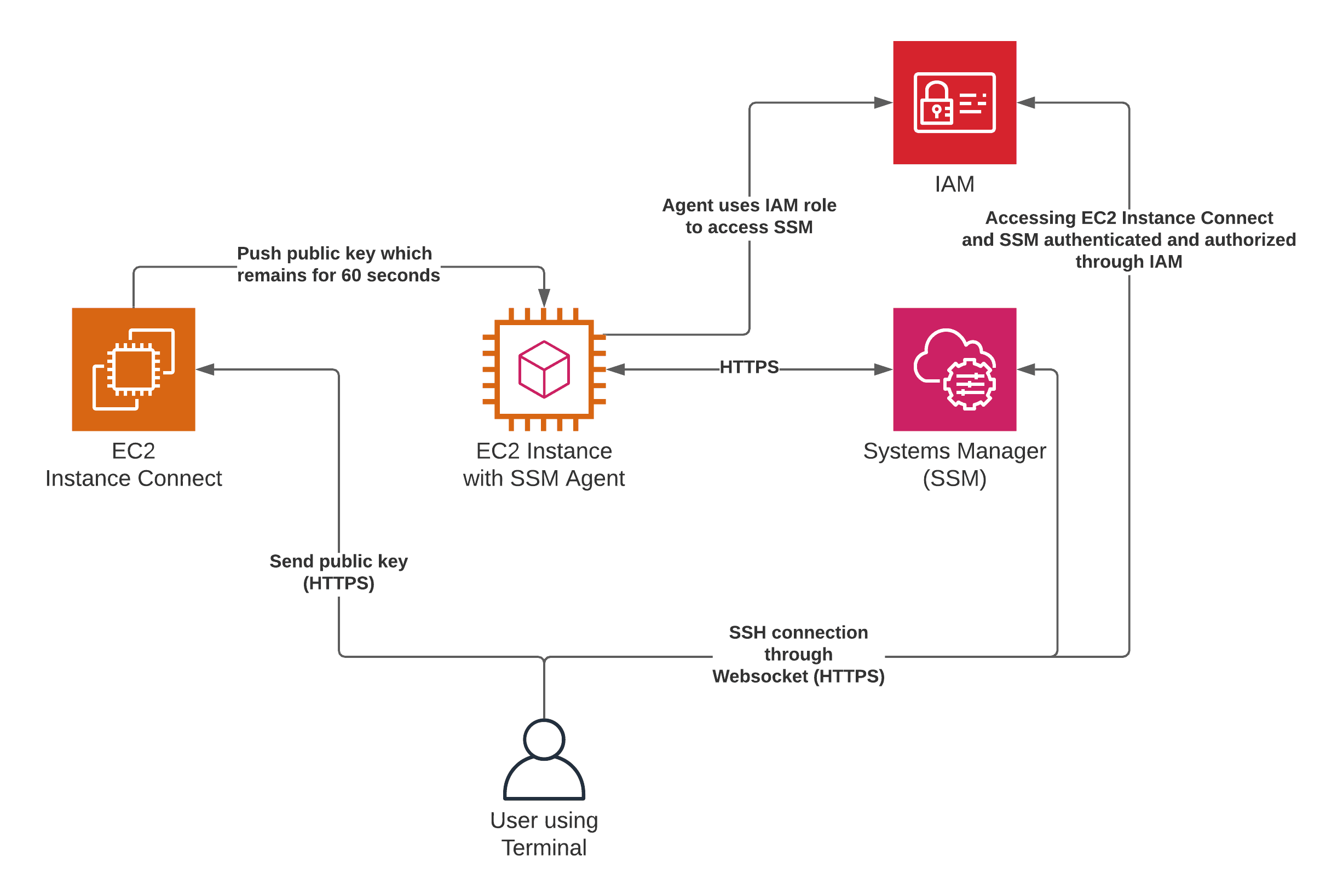
The journey to remote SSH access begins with your IoT device itself. Before you can connect, you need to ensure your device is properly configured. This involves installing and running an SSH server on your device. An SSH server acts as the intermediary, listening for incoming SSH connections and managing the secure communication. This server needs to be operational and properly configured with security measures, like strong passwords or key-based authentication, to prevent unauthorized access.
Once the SSH server is running on your device, the next step involves configuring your AWS environment. You'll need to create an IoT thing in the AWS IoT registry. An IoT thing represents your physical device within the AWS ecosystem. This step is crucial, as it provides a central point for device management and security. This device should be able to connect to the AWS IoT Device Gateway. This gateway is like a central hub that enables secure communication between your IoT device and the AWS cloud.
Within the AWS IoT ecosystem, you can leverage the "quick setup method" for establishing secure access. This approach utilizes the AWS IoT console to simplify the process. You can rotate access tokens and SSH into the remote device directly through your browser. Its a streamlined method designed for ease of use.
Alternatively, you can opt for the "manual setup method". This option requires you to manually configure the connection, providing more control over the process. Regardless of the method you choose, the primary goal is to establish a secure and reliable communication channel to your device.
Now, let's focus on the specifics for a Windows environment. You'll need an SSH client, such as PuTTY, to initiate the connection. PuTTY is a popular and free SSH client that allows you to connect to remote devices via SSH. After installing PuTTY, open the application and enter your device's IP address. Select "SSH" as the connection type and specify port 22, which is the default port for SSH. The next step is loading your private key into the PuTTY configuration.
If youre new to SSH key authentication, remember this crucial step: the private key is your personal key and must be kept secure. Never share your private key. The corresponding public key should be on the IoT device, which allows for a secure connection without entering a password each time. This method is more secure than using passwords and should be the standard.
With the IP address, connection type, port number, and private key configured, you can click "Open" in PuTTY. The client will then attempt to establish an SSH connection to your IoT device. If everything is correctly configured, you'll be prompted to log in using your device's credentials. Once logged in, you'll have remote access to your device via SSH.
For macOS users, the process is similar, but you can use the built-in terminal application, which already has an SSH client. You'll still need your device's IP address, SSH port (typically 22), and your login credentials or SSH keys. Open the terminal, type `ssh [username]@[device_ip_address]`, and press Enter. Replace `[username]` with your device's username and `[device_ip_address]` with your device's IP address. The terminal will then attempt to establish an SSH connection. If the connection is successful, youll be prompted for your devices credentials. Once authenticated, you have remote access to your IoT device.
The use of AWS IoT Core adds an extra layer of security. AWS IoT Core facilitates secure communication between your IoT devices and the AWS cloud, and provides a secure environment for accessing your devices. AWS IoT Core enables seamless integration with SSH for remote access. Furthermore, AWS IoT Device Management features, like Secure Tunneling, enhance security. This feature creates a secure tunnel through the AWS infrastructure, safeguarding your connection and reducing the risk of unauthorized access.
Troubleshooting is a critical aspect of IoT device management. AWS IoT Device Management can help diagnose and solve issues remotely, without the need for on-site intervention. By leveraging SSH over a secure connection, you can perform a variety of troubleshooting tasks, such as checking logs, restarting services, and updating configurations. This capability not only saves time and reduces costs but also allows for a quicker resolution of device issues.
One particularly useful approach for complex remote access is to use a "jump host" or "bastion host". This is a server that acts as an intermediary. You connect to the jump host first, and from there, you connect to your IoT device. This method enhances security by limiting direct exposure of your IoT devices to the internet. This is a very effective method for managing security and controlling access.
SocketXP is a cloud-based solution that provides SSH access to remote IoT devices. Solutions like SocketXP offer a hassle-free way to create secure tunnels for your devices. This method is especially helpful if youre behind a NAT router or firewall.
In the context of AWS, the use of Amazon EC2 Mac instances presents another option. With EC2 Mac instances, you have the full performance of a dedicated host. This can be beneficial if you need the raw processing power for a mac environment.
Remote access isn't just a "tech buzzword"; it provides real-world value. It equips you with the knowledge and tools to take your IoT projects to the next level. By learning how to connect SSH IoT devices over the internet using AWS on Windows and macOS, you unlock flexibility and control. You can securely and efficiently manage your IoT devices, regardless of their location.
Remember, there are free SSH tunnel options available. They simplify the process, giving you an easier way to connect your IoT devices. Always remember that security is of paramount importance. You're providing a secure channel over an unsecured network. The ability to control your IoT devices safely is key, and setting up a secure, efficient connection that meets your needs is an achievable goal.
AWS IoT ExpressLink is a recent development, making it faster and easier to develop. It streamlines the connection process, and gives you the best chance of succeeding in a quick manner. By setting up an EC2 instance, configuring security groups, and establishing an SSH tunnel, you can securely manage your IoT devices from anywhere in the world. This is a powerful tool for any IoT professional.
The choice between the quick setup and manual setup methods hinges on your technical proficiency and your need for customization. The quick setup is the easiest and fastest option, designed for immediate accessibility. The manual setup provides more control and is best suited for advanced users.
Secure tunneling is a vital feature, helping customers access remote devices over a secure connection. Secure Tunneling, offered by AWS IoT, offers a secure way to remotely access devices. This is particularly useful when the devices are behind NAT routers or firewalls.
In conclusion, successfully implementing remote SSH access to your IoT devices over the internet with AWS opens up a world of possibilities. It is a critical skillset. From improving efficiency, reducing costs, and increasing flexibility. By understanding the essential steps, leveraging AWS services, and prioritizing security, you can unlock the full potential of your IoT projects. With this knowledge, you are well-equipped to transform the way you manage and interact with your IoT devices.