SSH IoT Access: Free & Router-Friendly (No Windows Needed!)
Is it truly possible to remotely access and manage your Internet of Things (IoT) devices securely and efficiently, even when they're tucked behind a router, all without the need for a Windows operating system or a hefty price tag? The answer, surprisingly, is a resounding yes. With the right techniques and a little bit of know-how, you can achieve secure, remote access to your IoT devices, enabling you to monitor, control, and manage them from virtually anywhere in the world.
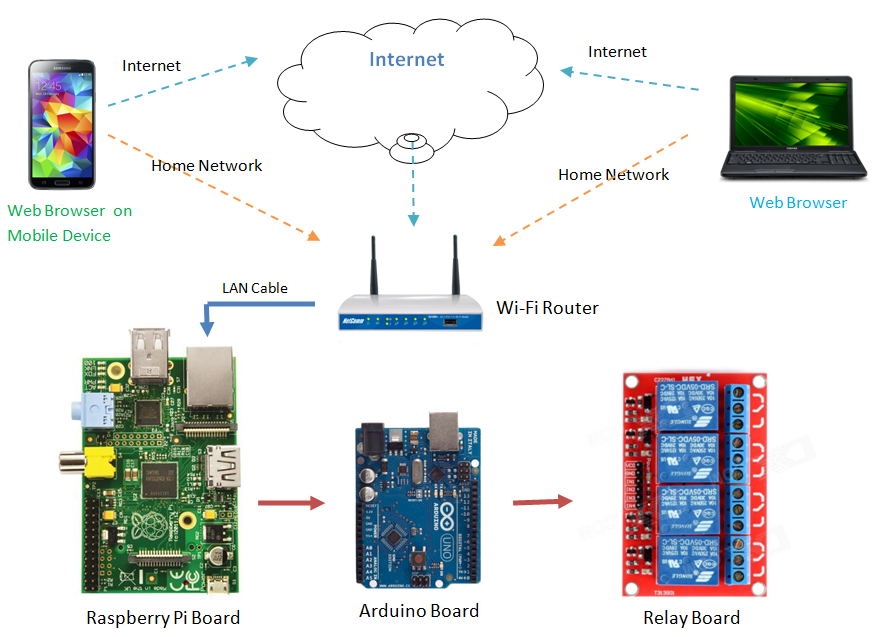
The challenge of connecting to an IoT device over the internet without relying on Windows can appear daunting at first glance, it's entirely achievable with the appropriate tools and understanding. This guide aims to break down the process, step-by-step, offering a clear path to setting up secure remote access for your devices. We will explore various techniques to ensure that your devices are accessible and secure, while simultaneously helping you understand the core components involved, such as SSH, port forwarding, and tools that simplify the process.
The foundation for secure remote access lies in understanding SSH (Secure Shell). SSH acts as a secure conduit, allowing you to establish a secure connection to your IoT devices. Through this encrypted channel, you gain a direct line of command to the device's operating system, enabling you to monitor, control, and manage it effectively. The process involves several steps, starting with enabling and configuring SSH on the IoT device itself. This is usually a straightforward process, often requiring the installation of an SSH server package and setting up a secure password or key-based authentication.
While SSH provides the core functionality, the real hurdle lies in navigating network complexities, especially when your IoT devices are behind a router. Typically, to access a device remotely, you would need to configure port forwarding on your router, directing traffic from a specific port to the internal IP address of the IoT device. However, this approach can be problematic, particularly if you don't have control over your router or are dealing with CGNAT (Carrier-Grade NAT), a common scenario in many internet service provider setups.
Fortunately, alternative methods exist that bypass the need for port forwarding, allowing you to establish a secure connection without directly exposing your device to the internet. One such method involves using a service like Pinggy, a free tool that creates a temporary public URL that tunnels traffic to your local SSH server. This approach effectively circumvents the complexities of port forwarding and firewall configurations, providing a seamless remote access experience.
To begin, youll need an IoT device that supports SSH, such as a Raspberry Pi or other embedded systems. Next, you must ensure that SSH is enabled and configured on the device. The configuration typically involves setting up a secure password or, ideally, using SSH keys for enhanced security. This is a crucial step as it protects your device from unauthorized access.
Once SSH is set up on your IoT device, the next step involves accessing it remotely. The traditional method involves port forwarding, which requires you to configure your router to forward traffic on port 22 (the default SSH port) to the internal IP address of your IoT device. However, as mentioned, this can be problematic. Therefore, the method we explore involves using tools that provide a secure tunnel to your device, avoiding the need for port forwarding entirely.
Using Pinggy, for instance, is a relatively straightforward process. You first download the Pinggy client on your device and then initiate a tunnel to your SSH server. Pinggy then generates a public URL that you can use to connect to your device from anywhere. This simplifies the connection process, eliminates the need for complex configurations, and makes it incredibly easy to remotely access your IoT devices.
Throughout this guide, we'll provide detailed instructions, tips, and best practices to ensure you can set up secure and efficient remote access for your IoT devices. From configuring SSH and setting up secure authentication methods to using tunneling services like Pinggy, we'll cover everything you need to know. The goal is to empower you with the knowledge and tools to control your devices from anywhere in the world, without relying on a Windows operating system and without spending a dime.
The benefits of being able to remotely access your IoT devices are immense. You gain the ability to monitor your devices from anywhere, enabling you to respond to issues promptly and ensure they are functioning correctly. Remote access also provides the flexibility to make configuration changes and update firmware. Essentially, remote access transforms how you manage and interact with your IoT devices, maximizing convenience, control, and security.
The power to manage your IoT devices remotely lies at your fingertips. By leveraging SSH, the underlying technology, and readily available tools, you can build a secure, accessible system. This will allow you to manage your devices. The freedom that is provided is remarkable, allowing you to be in control of your devices from anywhere, and anytime.
Let's begin by looking at the basics. SSH, or Secure Shell, is a cryptographic network protocol for secure data communication, remote command-line login, remote command execution, and other secure network services between two networked computers. SSH provides a secure channel over an unsecured network in a client-server architecture, connecting an SSH client application with an SSH server. The default port used by SSH is TCP port 22.
The key advantage of SSH is its security. It uses strong encryption to protect the data transmitted between the client and server, making it difficult for unauthorized users to intercept and read the information. SSH also offers authentication mechanisms to verify the identity of the users trying to connect to the server, further enhancing security. It is widely used for remote access to servers and devices, and for securely transferring files.
Now, imagine you have a Raspberry Pi setup at home, acting as a smart home hub, and you are traveling. Wouldn't it be convenient to be able to check the status of your sensors or control your lights remotely? The first step is to ensure SSH is enabled on your Raspberry Pi. Most Linux-based systems, including the Raspberry Pi, come with an SSH server pre-installed. You may just need to enable it. You would then configure a strong password or, preferably, use SSH keys for authentication.
The second step is dealing with your network. As mentioned earlier, if your Raspberry Pi is behind a router, you need a way to access it from the internet. Without port forwarding, this can be tricky. This is where tools like Pinggy, which create a secure tunnel, become invaluable. After installing Pinggy on your Raspberry Pi and running a simple command, you get a public URL. You can then use this URL with an SSH client like PuTTY (though this guide focuses on non-Windows methods), to connect to your device from anywhere in the world.
In our guide, we will cover all these steps. We'll explore the configuration of SSH, setting up secure authentication, and leveraging tools like Pinggy. You will learn the basics of the configurations, tools, and best practices to ensure your IoT devices are accessible and secure. The process is remarkably straightforward, with the greatest challenge being the initial understanding of the concepts. Once understood, managing your devices remotely becomes a routine task.
A critical aspect is to prioritize the security of your IoT devices. While SSH is a secure protocol, it's only as secure as the configuration you implement. Always use strong passwords or, even better, use SSH keys for authentication. Regularly update the firmware on your devices to patch any security vulnerabilities. Furthermore, consider using a firewall on your IoT devices to restrict access and monitor network traffic.
One of the most common questions is: Why not use port forwarding? Port forwarding is a method of making a computer on a private network accessible to devices on the internet. While it works, it also has downsides. Firstly, it exposes your device directly to the internet, increasing the risk of attacks. Secondly, it can be complex to configure, particularly if you're not familiar with your router's settings. Thirdly, as discussed earlier, it doesn't work if your device is behind CGNAT. The benefits of using Pinggy and similar tools include simplicity, enhanced security, and avoidance of the challenges associated with port forwarding.
Throughout this guide, we have focused on free methods. The beauty of this approach is that you don't need to invest in any expensive software or hardware. All the tools and techniques we'll be discussing are available free of charge, so you can build a secure and efficient remote access system without spending a dime. Free access to remote access is available to everyone, allowing anyone to have the potential to monitor and control their devices.
Let's recap the advantages: Firstly, you have the flexibility to manage your IoT devices from anywhere in the world. Secondly, you have a direct line of command to your device's operating system, which allows you to monitor, control, and manage your device. Thirdly, it enhances the security of your device, by avoiding the need to directly expose it to the internet. Finally, it's completely free of charge.
So, are you ready to take control of your IoT devices? With the right tools, knowledge, and a little bit of patience, you can make this a reality. Let's dive in and explore the step-by-step process, configurations, tools, and best practices. By the end of this guide, you'll have the knowledge and tools needed to set up secure and efficient remote access to your IoT devices, and you'll be amazed at how much you can achieve with a little bit of know-how. The journey to remote access to your IoT devices is now within your reach.
To summarize, the key components of the remote access setup include: the IoT device (e.g., a Raspberry Pi), SSH installed and configured on the device, a secure network connection, and a tool like Pinggy to create a secure tunnel.
With these components in place, you can enjoy the benefits of remote access to your IoT devices, and your devices will be at your fingertips. Remember that with the right tools, knowledge, and a bit of patience, you can make this a reality and remotely access your devices from anywhere.
To use SSH, the IoT device must support SSH, and SSH must be enabled and configured on the device.
Open putty and enter your servers IP address in the host name field, Click open to connect to your server, SSH server listens on tcp port 22 by default. But without port forwarding, if your raspberry pi is behind NAT or firewall or CGNAT, you will not be able to access your device.
This article will guide you through the process of connecting to your IoT device via SSH without relying on a windows operating system and without spending a dime.
In this guide, we will explore how to use remote IoT behind a router without windows, completely free of charge.
| Feature | Description | Details |
|---|---|---|
| SSH (Secure Shell) | A cryptographic network protocol for secure data communication. | Provides secure remote access and command execution. Uses encryption to protect data. |
| IoT Device Support | Devices must support SSH. | Enable SSH and configure it on the device. |
| Operating System Independence | Allows remote access without Windows. | Uses alternative tools and methods. |
| Cost | Free. | Uses open-source tools and methods. |
| Remote Access | Access devices from anywhere. | Use the methods to connect via SSH. |
| Port Forwarding | Avoids the need for port forwarding. | Use alternative tools. |