AWS IoT Secure Tunneling: SSH Access To Remote Devices - Tutorial
Is it possible to securely access and manage Internet of Things (IoT) devices deployed in remote locations, even when they are behind firewalls that restrict inbound traffic? The answer is a resounding yes, and the key lies in leveraging the power of secure tunneling provided by AWS IoT Core.
The proliferation of IoT devices across diverse industries has created a pressing need for efficient remote device management. These devices, often deployed in challenging environments, require regular maintenance, troubleshooting, and configuration updates. However, traditional methods of accessing these devices, such as sending technicians on-site or relying on complex firewall configurations, can be costly, time-consuming, and insecure. Secure tunneling offers a robust and streamlined solution to these challenges, enabling secure, bi-directional communication with remote devices over a connection managed by AWS IoT.
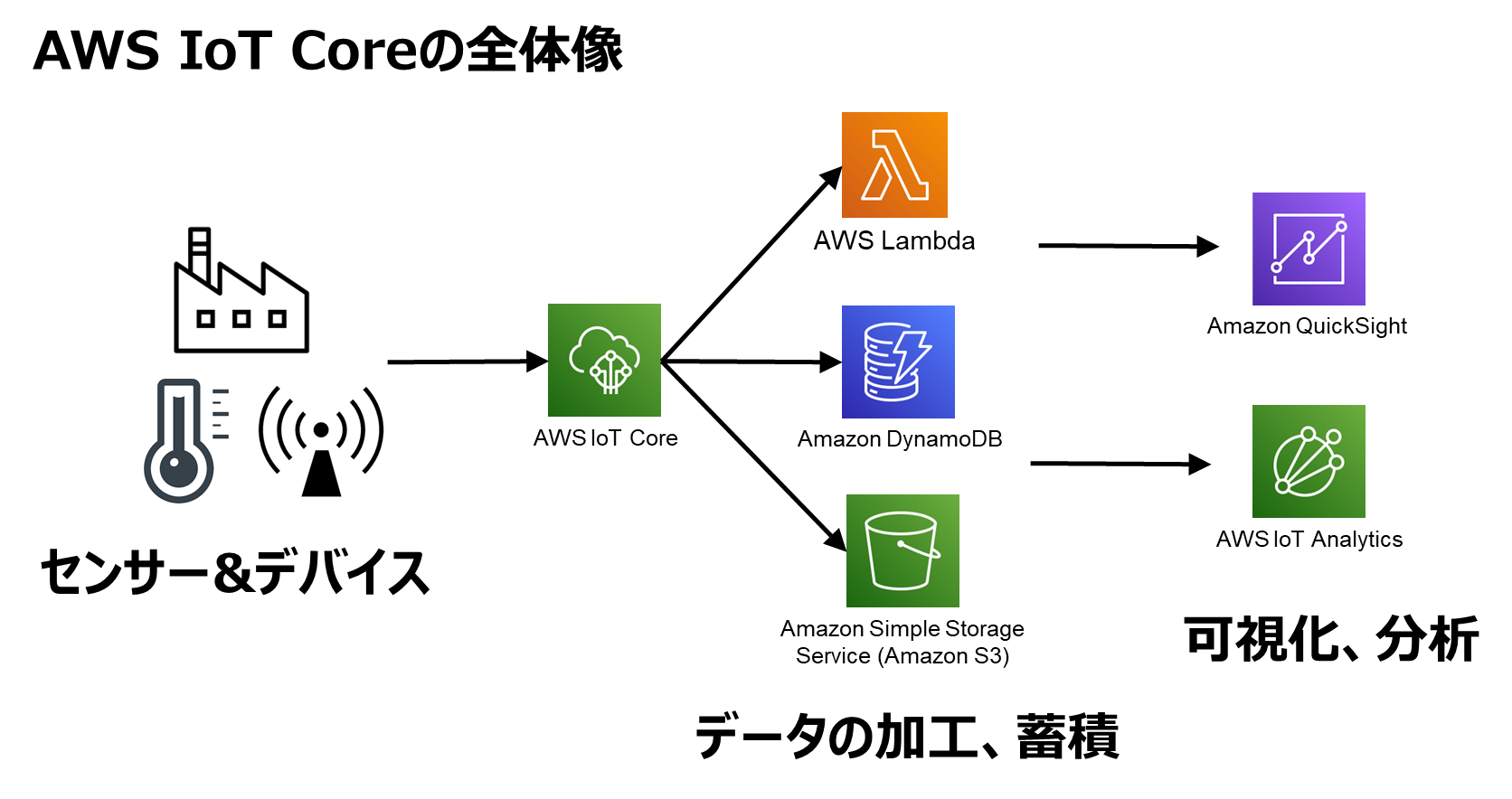
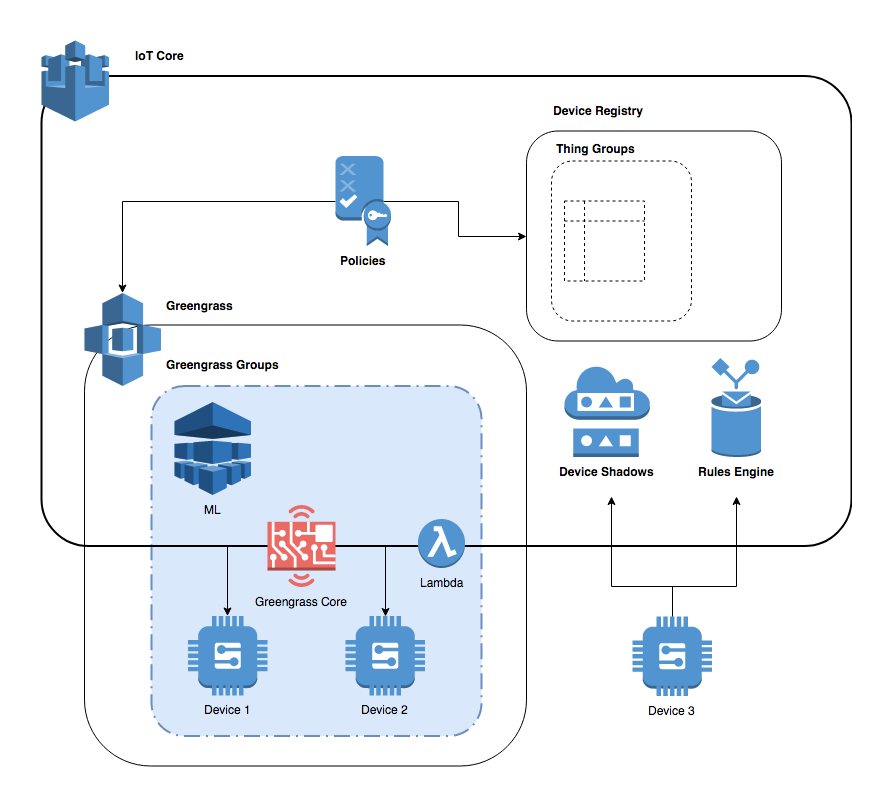
At the heart of this solution lies the concept of an "IoT thing," which serves as the digital representation of your remote device within the AWS IoT registry. Think of it as the device's identity in the cloud. This "thing" is then associated with an IoT device agent running on the remote device itself. This agent is configured to connect to the AWS IoT Device Gateway and subscribe to specific MQTT topics, facilitating communication with the cloud platform.
One of the primary benefits of secure tunneling is its ability to bypass the limitations imposed by firewalls. By establishing a secure, outbound connection from the remote device, secure tunneling eliminates the need to modify existing firewall rules to allow inbound traffic. This simplifies network management and maintains the security posture of the remote site. Furthermore, the use of secure tunneling does not necessitate updates to your existing inbound firewall rules, allowing you to maintain the same level of security provided by the firewall rules at a remote location.
The use of AWS IoT Core for secure tunneling also brings the advantages of reduced costs compared to traditional methods of accessing the device. With the service initiation, the cost has decreased which makes it a budget friendly option.
Secure tunneling offers several methods to establish a connection, including the quick setup method, which allows you to rotate access tokens and securely SSH into the remote device directly from within your web browser. To utilize this quick setup, you must have already created an IoT thing in the AWS IoT registry.
The ability to securely connect to remote devices is invaluable in various applications. In the healthcare industry, secure tunneling facilitates remote patient monitoring and the management of medical devices. In the industrial sector, it enables remote diagnostics and maintenance of equipment, reducing downtime and improving operational efficiency.
AWS IoT Core acts as the "Swiss Army knife" of IoT platforms. By integrating with other AWS services like AWS Systems Manager and AWS CloudFormation, AWS offers a robust infrastructure for secure and scalable remote access to your IoT devices. The foundation of this secure communication rests on the AWS IoT Core, which simplifies the process of accessing your IoT devices remotely.
Consider, for example, a scenario where a Raspberry Pi is used as an IoT device. To enable remote access, SSH can be enabled on the Raspberry Pi. This can be followed by AWS IoT Greengrass v2 configuration to further establish a secure connection. For detailed information, you can refer to the Raspberry Pi documentation for SSH setup. If you face any difficulties configuring the device, other options exist, such as creating a virtual device with Amazon EC2 or using a Windows, Linux, or Mac PC as an AWS IoT device. This flexibility ensures that remote access is achievable regardless of the specific hardware or operating system.
The future of IoT SSH connect AWS looks bright. As technology continues to evolve, we can expect even more advanced features and capabilities. These include the potential for processing data closer to the source, reducing latency and improving performance, which will further enhance the efficiency and responsiveness of remote device management.
Beyond the technical aspects, the economic advantages of secure tunneling are also significant. By eliminating the need for on-site visits from technicians to troubleshoot and maintain devices, secure tunneling reduces operational costs and improves overall efficiency. With its powerful services, AWS makes it easy to secure and scale remote access for your IoT devices.
The convenience of secure tunneling extends beyond simple access. It offers the ability to create a tunnel and send a token to the device, allowing you to connect to the device from the AWS IoT console. This makes it simple to manage devices without the need for direct physical access.
However, it's essential to note that while the username and password login via SSH through the AWS IoT console works effectively, login via private key might not be as straightforward. Even if the private key functions correctly on the local network, it may not work directly when utilizing the secure tunnel. This is an important aspect to consider when setting up SSH access.
This approach, combined with the use of secure tunneling, provides a flexible and cost-effective solution for managing devices, offering a seamless experience for users.
In the context of the Japanese language content included, the core concept remains the same: Secure tunneling, based on AWS IoT Core's device management capabilities and browser-based SSH functionality, enables remote device login.
From a high level of overview, when devices are deployed behind restricted firewalls at remote sites, you need a way to gain access to those devices for troubleshooting, configuration updates, and other operational tasks. Secure tunneling, a feature of AWS IoT Device Management, solves this. The ease of access and management is one of the primary goals of secure tunneling. With a secure connection, you can easily make updates and monitor performance.
By leveraging secure tunneling, organizations can achieve a new level of control over their remote IoT devices. This provides a way to gain access to those devices for troubleshooting, configuration updates, and other operational tasks. The future of remote device management is undoubtedly connected to secure tunneling, and AWS IoT Core is leading the way.