IOT Remote Access: Securely Access & Manage Your Devices
Are you prepared to unlock the full potential of your Internet of Things (IoT) devices, regardless of their physical location? Embrace the transformative power of remote access, a critical enabler for efficient management, enhanced security, and unprecedented control over your interconnected world.
In today's rapidly evolving technological landscape, the proliferation of IoT devices has revolutionized industries and reshaped our daily lives. From smart homes and industrial sensors to connected vehicles and sophisticated retail systems, these devices are generating vast amounts of data, driving operational efficiencies, and creating entirely new possibilities. However, with this widespread adoption comes the challenge of effectively managing and securing these distributed devices, particularly those deployed in remote locations or behind complex network configurations.
Firewalls, the indispensable guardians of network security, often pose a significant hurdle to remote access. While they diligently protect IoT devices from unauthorized external intrusions, they simultaneously impede the ability to connect to and manage these devices remotely. This inherent paradox necessitates innovative solutions that can bridge the gap between robust security and seamless remote access.
Historically, troubleshooting and maintaining IoT devices deployed at remote sites has been a costly and time-consuming endeavor. Often, technicians had to be dispatched on-site to establish a physical connection to the device, diagnose the issue, and implement the necessary repairs or updates. This process increased complexity, inflated operational costs, and hindered the agility of businesses relying on these devices.
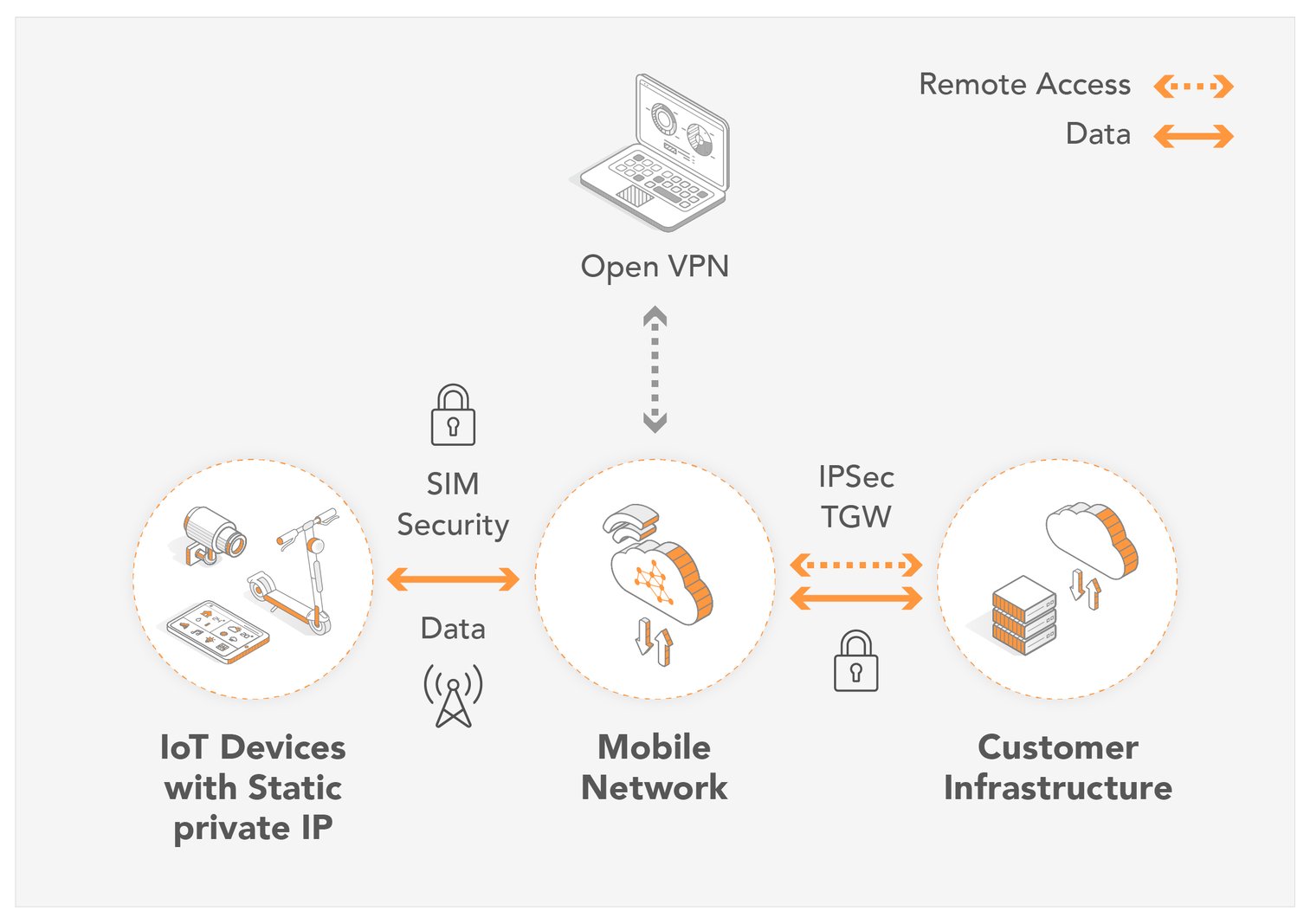
Now, let's delve into the core of the matter: How can we effectively set up and secure remote access to your IoT devices, empowering you to manage, monitor, and control them from anywhere in the world? While the specific steps required will vary depending on the type of device, the manufacturer, and the network configuration, there are general principles and best practices that can guide you through the process.
Remote access to IoT devices is more than just a convenience; it's a fundamental requirement for efficient and secure device management. With the ability to connect, monitor, and control devices remotely, administrators can proactively address unauthorized activity before any potential damage is inflicted.
Let's consider the benefits of leveraging remote access for your IoT devices. Besides preventing and resolving security breaches, remote access enhances the inherent capabilities of wireless interconnectivity. This allows businesses to realize several key benefits:
- Cost Savings: Reduce the need for on-site visits, minimizing travel expenses, technician time, and overall operational costs.
- Increased Efficiency: Resolve issues and implement updates swiftly, reducing downtime and ensuring optimal device performance.
- Enhanced Security: Proactively monitor device activity, detect and address security threats promptly, and prevent data breaches.
- Improved Agility: Respond quickly to evolving business needs, update device configurations remotely, and rapidly deploy new features.
- Centralized Management: Manage a distributed fleet of devices from a central location, streamlining operations and reducing administrative burden.
Several solutions are available for enabling secure and reliable remote access to IoT devices, each with its unique features and capabilities. One such solution is SocketXP, a cloud-based IoT device management and remote access platform. It works seamlessly without requiring any modifications to your Wi-Fi router or firewall settings. Another option is Qbee.io, which offers an integrated and highly secure remote access solution, enabling access to any device port, even behind firewalls. Further, Huawei Cloud IoT Device Access (IoTDA) offers a comprehensive approach, allowing you to connect your physical devices to the cloud for data collection and remote control.
Lets examine some core elements for setting up remote access to IoT devices:
- Secure Device Authentication and Authorization: Implement robust authentication mechanisms, such as multi-factor authentication, to verify user identities and prevent unauthorized access.
- Network Segmentation: Isolate IoT devices from the broader network to limit the impact of potential security breaches.
- Regular Security Audits: Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses.
- Data Encryption: Encrypt all data transmitted between the remote access platform and the IoT devices to protect against eavesdropping and data tampering.
- Firewall Configuration: Configure firewalls to restrict access to specific IP addresses and ports, minimizing the attack surface.
- Logging and Monitoring: Implement comprehensive logging and monitoring to track device activity, detect suspicious behavior, and provide valuable insights for security incident response.
Furthermore, remote access empowers users to interact with their devices from any location, be it adjusting the thermostat at home while at work or monitoring industrial equipment performance from a different site. This ability to control and monitor devices remotely enhances efficiency and productivity.
With a VPN, you can access your IoT device from anywhere with an internet connection. Whether youre in another country or on the move, you can control and monitor your device as if you were physically present.
Implementing an IoT device management and remote monitoring platform helps you manage, access, monitor, update, and control numerous IoT or embedded Linux devices in various locations.
Take full control of your IoT devices remotely with Remote Desktop Protocol (RDP). In essence, RMS Connect functions as a centralized hub for engineers and IT administrators to remotely access, manage, and control end devices connected to their fleet of remote IoT devices. By leveraging such a remote device management system, accessing and controlling your device fleet and performing IoT device remote tasks becomes straightforward.
For a more robust and feature-rich solution, consider upgrading to a professional or enterprise plan, which offers key advantages, including remote IoT pricing, comprehensive remote device management, and business-secure access along with enhanced IoT monitoring capabilities.
Here are five key tips for businesses looking to effectively manage their IoT devices remotely:
- Choose a Secure Platform: Select an IoT device management and remote access platform that is trusted by numerous customers worldwide, ensuring secure management and remote access for your IoT device fleet.
- Prioritize Security Best Practices: Follow the security best practices and guidelines to fortify your IoT devices against potential security threats.
- Centralized Management: Utilize an IoT device management platform that supports remote access, ensuring streamlined operations.
- VNC Client: Connect to your IoT devices remotely via the TightVNC client from a Windows or Mac laptop over the internet.
- XFCE Desktop Environment: Set up the XFCE desktop environment on your IoT device.
A well-structured approach to mitigate risks and optimize performance is required for effective and secure IoT remote control.
In essence, remote access is not just a feature; it's a necessity for any organization deploying IoT devices. It empowers businesses to manage, monitor, and control their devices with greater efficiency, enhanced security, and unparalleled flexibility. By embracing the principles and technologies discussed in this article, you can unlock the full potential of your IoT investments and propel your business toward success.
Now, lets talk about solutions.
Utilize a secure IoT device management and remote access platform like SocketXP, trusted by countless customers globally, for secure management and remote access to your IoT device fleet. It provides secure tunnels to the SSH port or other network services of your remote devices, accessible over the internet without requiring static IP addresses or port forwarding. The platform is designed for secure remote access, control, and management of IoT and embedded Linux devices, raspberry pi fleet, or other linux machines behind a NAT router and firewall.
Qbee.io offers an integrated and highly secure remote access solution that enables access to any device port, even behind firewalls, using a lightweight agent and cloud-based management platform, providing secure remote access, monitoring, and control for your IoT devices.
Huawei Cloud IoT Device Access (IoTDA) allows you to connect your physical devices to the cloud, where you can collect device data and deliver commands to devices for remote control. It also integrates with other Huawei cloud services to help you develop IoT solutions rapidly. It supports secure device access, data transmission, and device management capabilities to help you manage and control your IoT devices from a central location.
Torizon's remote access is the ideal field debugging solution. Debug and configure your remote IoT devices as if they were within reach.
The remote IoT platform allows users to remotely control IoT devices using a web browser.
Users can set up a VNC server on a Raspberry Pi and use a VNC client application on a device of choice to view and interact with the Pi's desktop from anywhere with an internet connection.