Secure IoT Access: Master SSH & Remote Control From Anywhere
Is it possible to remotely manage your Internet of Things (IoT) devices from anywhere in the world, securely and efficiently? The answer is a resounding yes, thanks to the power of Secure Shell (SSH).
The world of interconnected devices has exploded in recent years. From smart homes to industrial automation, IoT devices are collecting, processing, and transmitting vast amounts of data. Managing these devices, often deployed in remote locations, requires a secure and reliable method of access. SSH, a network protocol, provides this essential functionality.
Before diving deeper, let's understand the core elements. Setting up SSH for your IoT devices essentially means establishing a secure connection that allows you to control, troubleshoot, and update your devices remotely. This guide will walk you through the necessary steps, ensuring that your IoT setup remains secure and accessible.
We begin with the very foundation of a stable system, the installation of a fresh and clean Linux installation on your server. This foundation will be vital as we move forward to ensure the utmost security and efficient management of our connected devices.
Once the Linux operating system is successfully installed, the subsequent steps involve setting up remote access. This guide is structured into distinct sections, providing you with a comprehensive understanding of how to remotely access an IoT device via SSH from a web browser. The initial focus will be on setting up secure SSH keys, configuring IP addresses, and adjusting router settings. Following this, the installation of the VNC server software and launching the VNC client application will enable graphical access. The process is designed to be straightforward, eliminating the need to discover the IoT device's IP address and change firewall settings.
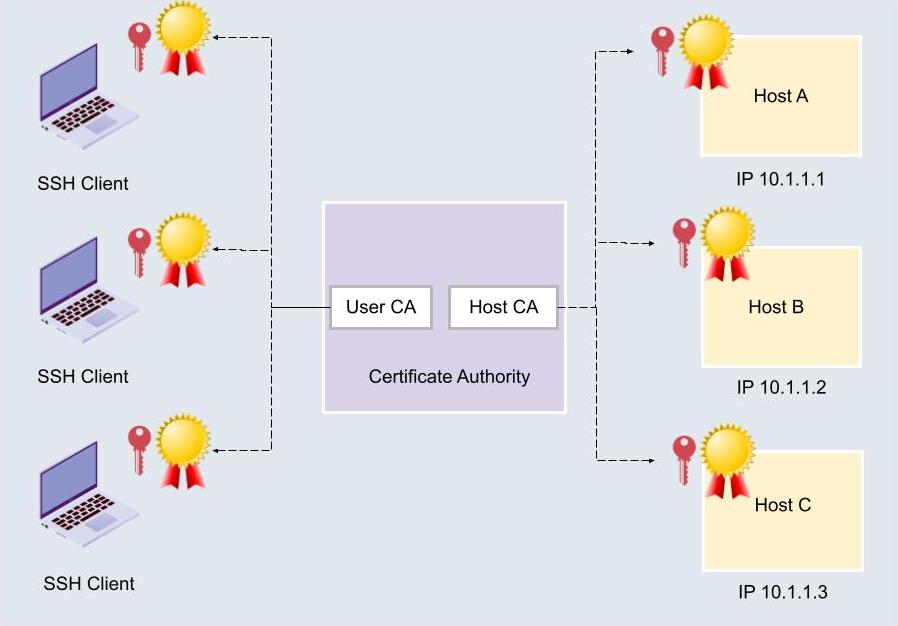
A critical advantage of SSH is the security it provides. All data transmitted through an SSH connection is wrapped within an encrypted tunnel, ensuring confidentiality and preventing unauthorized access. Whether you choose to SSH into your IoT device using the system user or secure authentication based on SSH keys, coupled with standard client tools like PuTTY, you gain comprehensive control.
This comprehensive guide gives you full control of your Linux server or device. With our expert tips and tricks, you can unlock the full potential of your Linux server, allowing you to access it from anywhere, at any time.
For those whose devices are not based on Ubuntu Linux, or for those seeking a deeper understanding of SSH server and client configuration, the subsequent sections provide detailed instructions. These sections cover the installation and configuration of SSH servers and clients, including the generation of SSH public/private keys for secure remote access.
OpenSSH is a vital component for secure remote access to your IoT devices. This free, open-source software uses the SSH protocol, which is the bedrock of creating secure, encrypted communication channels over computer networks. Essentially, it acts as the digital key that unlocks the potential of remote device management.
Lets take a closer look at the technical process. For instance, accessing the SSH of a Jetson Nano device from your laptop demonstrates a practical application. Through the use of a local endpoint, you can access the Jetson Nano's SSH server, offering a clear and straightforward way to initiate and maintain a secure connection.
The SSH protocol is an ideal solution for managing IoT devices remotely. By setting up SSH on your IoT devices, you guarantee that your data is protected from unauthorized access, ensuring that you can securely manage your setup with ease.
The device stream creation process involves a negotiation between the device, service, and IoT hub's main and streaming endpoints. This enables secure remote access to manage your IoT devices from anywhere in the world, with SSH providing a robust, encrypted connection.
The ease with which SSH allows you to access and manage your IoT devices is truly remarkable. Whether you're updating firmware, troubleshooting issues, or simply monitoring device status, SSH provides the necessary tools and capabilities.
To reiterate, here's a concise guide to setting up SSH for your IoT devices:
- Ensure SSH is enabled on the IoT device.
- Configure the SSH server on your IoT device.
- You'll need to set up an SSH client on your machine.
- Configure port forwarding on your router.
- Ensure your IoT device is accessible.
The configuration of the SSH server on your IoT device is where the magic happens. It involves enabling SSH, creating user accounts, and setting up authentication methods, such as using passwords or SSH keys. This ensures that only authorized individuals can access your devices.
Secure shell (SSH) is the cornerstone of remote access tools, enabling you to manage your IoT devices from virtually anywhere. By employing SSH, your connection is encrypted, guaranteeing the safety of your data, regardless of the underlying operating system, whether it be Ubuntu, Windows, or any other platform.
To install and run an SSH server on your IoT device, execute the following commands:
- First update your linux
- Then install the openssh server.
- The following commands will enable and run ssh server as a daemon in the background.
- Then enable ssh server and start it.
Setting up the SSH server on your IoT device is a crucial step. The SSH server will function as a secure file server, understanding SFTP/SCP protocols. This enables secure file transfers.
We will use SCP/SFTP client software (like PuTTY PSFTP/FileZilla) that implements SSH-based secure file transfer protocols such as SFTP/SCP to transfer files.
Security should be your top priority when working with IoT devices, and SSH keys are a great first step. It's an excellent first step, but it's important to take additional measures to safeguard your setup.
Securing your IoT setup with SSH keys offers a robust layer of security. Here are a few tips to help fortify your IoT security:
- Change the default SSH port to something less obvious.
- Regularly update your devices' firmware and software.
- Implement strong passwords and consider multi-factor authentication.
- Monitor your network traffic for suspicious activity.
- Restrict access to your devices to only authorized users and devices.
VNC (Virtual Network Computing) enables the remote access of the IoT graphical user interface (GUI) or desktop, offering safe access. The combination of convenience and security measures makes SSH a perfect choice for remote IoT device management.
With SSH configured and secured, managing your IoT devices becomes remarkably straightforward. Whether you're controlling a smart thermostat or monitoring a security camera, SSH gives you the ability to manage it all from your machine.
The use of SSH is not limited to specific operating systems or devices; it's a versatile tool that can be adapted to diverse IoT environments. This flexibility makes it an essential skill for anyone working with connected devices.
Here are a few things you can do:
- Update firmware on your iot devices;
- These clients allow you to connect to your devices from any browser, making remote access more accessible than ever.
- Configure the local proxy when using the manual setup method and connect to the tunnel to access the destination device.
- Ssh into the remote device from a browser without having to configure the local proxy.
The capability to remotely access and manage your IoT devices via SSH is a powerful tool, streamlining the management of your smart devices. By following the instructions, you can ensure remote control, making it possible to troubleshoot, update, and manage your devices with ease and security.
For this challenge, youll be using device streams to set up an SSH connection to the simulated iot device youve been using, and then locking down firewall to confirm that a connection is still possible.
SSH is a network protocol that provides secure remote access over an insecure network. The ability to access IoT devices over the internet using SSH and understanding the underlying security protocols is crucial in today's interconnected world.
In essence, using SSH with IoT devices offers a robust, encrypted tunnel for remote access, ensuring data protection and control over your devices from anywhere in the world.
Here's a simple overview of steps required:
- Ensure SSH is enabled on the IoT device.
- Install and configure an SSH client on your local machine.
- Configure port forwarding on your router (if accessing from outside your local network).
- Connect to your IoT device via SSH.
These steps outline the basic process; the specific commands and configurations will vary slightly depending on your device and operating systems, but the overall workflow remains consistent.
The significance of securing your IoT setup with SSH cannot be overstated. While SSH keys are a great first step, there's more you can do to keep your setup safe. A key consideration is to change the default SSH port to something less obvious. This simple act can significantly reduce the risk of automated attacks.
Here's a detailed table summarizing the key aspects of setting up and using SSH for IoT devices:
| Aspect | Description | Implementation | Security Considerations |
|---|---|---|---|
| SSH Protocol | Secure Shell - A network protocol that enables secure remote access to a device. | Enables secure file transfers and remote shell access. | Encryption, authentication, and secure communication. |
| SSH Server | Software installed on the IoT device that listens for SSH connections. | Installation and configuration of OpenSSH or a similar server. | Regularly update server software and implement strong authentication. |
| SSH Client | Software used to connect to the SSH server. | Examples: OpenSSH (Linux/macOS), PuTTY (Windows). | Secure your client installation and environment. |
| SSH Keys | Public/private key pairs used for authentication. More secure than passwords. | Generate key pairs, copy the public key to the IoT device. | Protect your private key. Don't share it. |
| Port Forwarding | Configuring your router to allow external access to your IoT device via SSH. | Requires accessing your router's configuration. Forward port 22 (or your custom port). | Use a strong router password. Securely configure the firewall. |
| Firewall Configuration | Configuring the firewall on your IoT device to allow SSH traffic. | Allowing traffic on port 22 (or your custom port) for inbound connections. | Restrict the allowed IP addresses for SSH access. |
| SFTP/SCP | Secure File Transfer Protocol/Secure Copy Protocol - Secure protocols for file transfer. | Use an SFTP or SCP client (e.g., FileZilla, psftp) to transfer files securely. | Verify the integrity of transferred files. |
| VNC (Virtual Network Computing) | A protocol for remotely accessing the IoT device's graphical user interface (GUI) or desktop. | Setting up a VNC server on the device and a VNC client on your computer. | Secure VNC connections. Use SSH tunneling for added security. |