IoT Security: Focus On This First! [IoT, VPC, AWS]
Is the Internet of Things (IoT) poised to revolutionize our world, and if so, how can developers ensure its secure and efficient implementation? The answer lies in prioritizing robust security measures and understanding the intricacies of network infrastructure, particularly within the realm of virtual private clouds (VPCs).
The proliferation of IoT devices, from smart appliances to industrial sensors, presents both unprecedented opportunities and significant challenges. As these devices generate and transmit vast amounts of data, ensuring its confidentiality, integrity, and availability becomes paramount. This is where a keen focus on secure development practices and network architecture is indispensable. Specifically, developers of IoT applications must consider a variety of factors, including device authentication, data encryption, and secure communication protocols. A common approach involves the implementation of private networks to comply with diverse industrial regulations, thus offering critical data privacy and security encapsulation.
This article delves into the crucial aspects of IoT development, exploring the technologies and strategies that enable secure and reliable IoT deployments. We will examine how cloud service providers are leveraging advanced networking capabilities to create robust and resilient solutions, with a particular focus on the role of Amazon Web Services (AWS) and its services.
One of the first considerations for developers of IoT applications should be a comprehensive security strategy. This encompasses the entire lifecycle of the device, from its design and manufacturing to its deployment and ongoing operation. Security best practices must be implemented at every stage, including secure boot processes, regular firmware updates, and robust authentication mechanisms. AWS provides a suite of tools and services designed to facilitate secure IoT deployments. AWS IoT Core, for example, allows you to connect devices to the cloud securely and manage them at scale. Additionally, services like AWS IoT Device Defender can help monitor and audit your fleet of devices for security vulnerabilities.
Beyond security, the network infrastructure plays a critical role in enabling secure and efficient IoT deployments. Private networks offer a powerful approach to safeguarding sensitive data and ensuring reliable communication between devices and cloud services. These networks provide an isolated environment, protecting data from unauthorized access and reducing the risk of cyberattacks. Many IoT service providers are now leveraging AWS services to enhance their private networks for tasks such as MQTT (Message Queuing Telemetry Transport) message transmission and data transmission.
AWS has a long history of providing robust tools and services for its clients, it is essential to comply with all the industrial regulations by using private networks for the IoT services, with the help of AWS, such as MQTT message transmission and safeguarding data transmission.
Lets explore a hypothetical scenario. Consider an industrial facility that deploys an IoT system to monitor and control its HVAC (Heating, Ventilation, and Air Conditioning) system. The facility needs to ensure that the data generated by the system is protected from unauthorized access and that the system itself is resilient to cyberattacks. In this instance, the implementation of a private network, using AWS services would be an ideal solution.
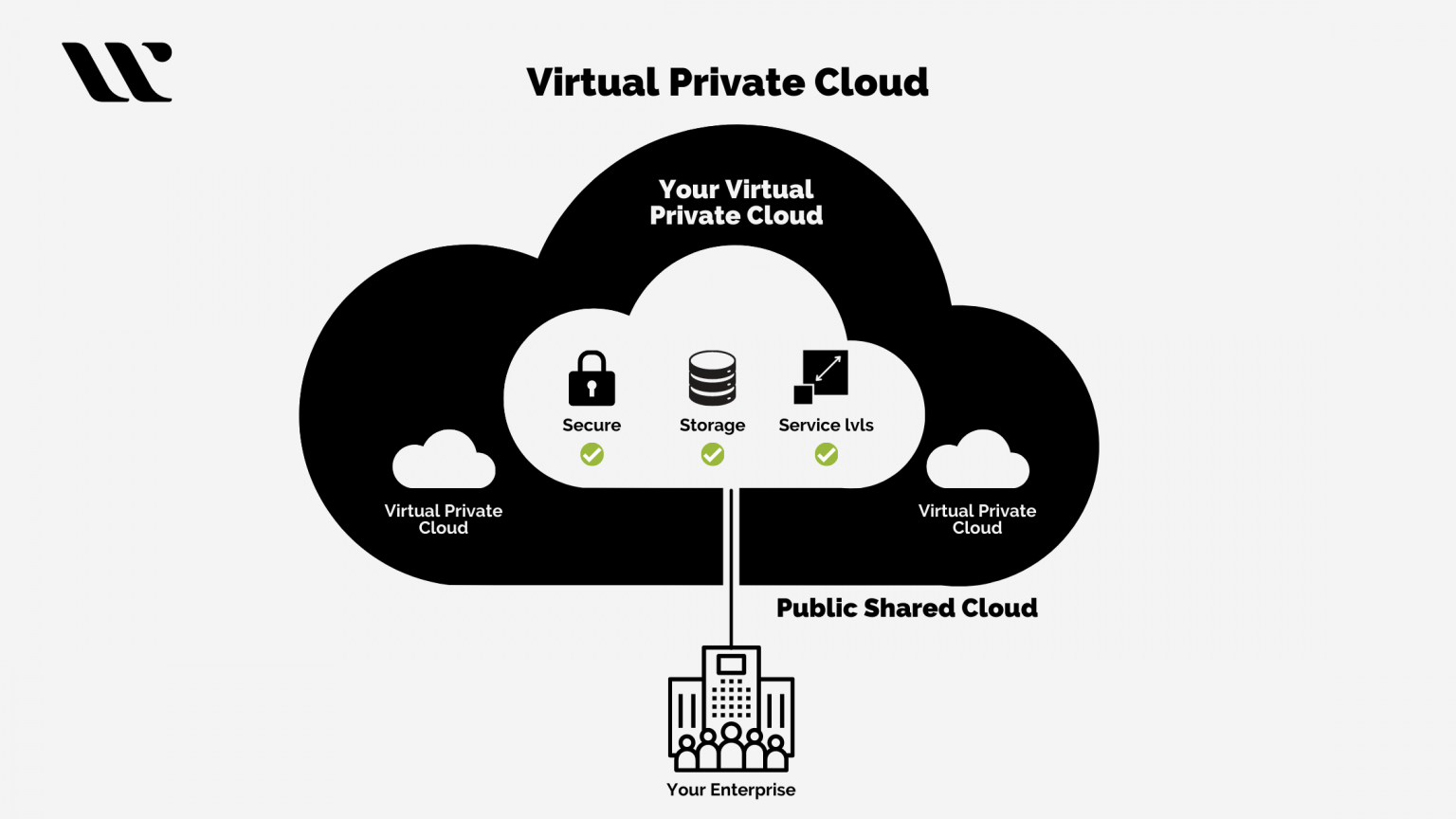
By utilizing AWS IoT Core in conjunction with a Virtual Private Cloud (VPC), the facility can create a secure and isolated network environment. This VPC acts as a logically isolated section of the AWS cloud, where the facility can launch its resources in a virtual network it defines. Within the VPC, the facility can establish private endpoints for its IoT Core data, enabling communication between its devices and the AWS IoT Core service entirely within the AWS network. This approach leverages the power of AWS PrivateLink, a technology that allows private communication between your VPC and AWS services, by using private IP addresses that are not exposed to the public internet. This ensures data confidentiality and reduces the risk of interception or tampering.
Moreover, the facility can use AWS IoT Device Defender to monitor its devices for security vulnerabilities and anomalies. This service helps identify potential threats, such as compromised devices or unusual network traffic, and enables the facility to take proactive measures to mitigate risks. In this scenario, the security posture of the IoT solution is significantly improved, ensuring that the HVAC system operates securely and reliably.
For the proper functionality of this whole system of AWS, it is very important to know how the system works, The "Amazon Virtual Private Cloud" (Amazon VPC) allows users to create an isolated section of the AWS cloud, which they can configure to create a virtual network. It gives complete control of your networking environment. The user has the ability to select its own IP address range, create subnets, and configure route tables and network gateways. With the use of Azure Private Link, the users can set up a private endpoint for the IoT hub to make sure that the services inside your Vnet can access IoT hub without sending traffic to its public endpoint. The users can create a Virtual Private Cloud (VPC) using the CreateTopicRuleDestination API or using the AWS IoT Core console.
In essence, it creates a secure and isolated network environment within the AWS cloud, enabling businesses to deploy and manage resources with complete control over network settings, security, and access. This approach offers significant advantages over traditional network configurations, including enhanced security, improved performance, and greater flexibility. Cloud networking is the use of cloud computing technologies and services to optimize and manage network infrastructure and resources.
For industrial sectors, it is very important that their data should not be leaked, so that is why private networks can help the IoT service providers deploy solutions which provide critical data privacy and security encapsulation, there are certain industrial regulations that need to be followed.
For the security analyst for a smart home device manufacturer, the most critical security measure is implementing end-to-end encryption for all data transmitted between devices and the cloud.
The convergence of cloud computing and the Internet of Things is transforming various industries, including healthcare, manufacturing, and transportation. Cloud computing provides the infrastructure, scalability, and flexibility needed to support the massive influx of data generated by IoT devices. By leveraging cloud services, organizations can analyze this data, gain valuable insights, and make data-driven decisions. The cloud enables organizations to store and process data, deploy and manage applications, and scale their operations as needed. One of the primary benefits of cloud computing is its ability to reduce costs and improve efficiency.
In addition to security and network infrastructure, it is very important to select a deployment model that is suitable for their specific requirements. A hybrid cloud deployment model offers a balanced approach by combining the advantages of both private and public clouds. This model allows organizations to store sensitive data in a private cloud while leveraging the scalability and cost-effectiveness of the public cloud for less sensitive workloads.
The utilization of IoT technology is also a prime target for cyber attacks, with the use of connected devices exchanging data on networks, IoT can be a high-risk target. In that case, either Active Directory or certificates will be used for authentication. It is very important to secure an HVAC system that is part of an IoT network from data exfiltration exploits. The security specialist needs to secure the network traffic, the device firmware, data storage, and API interfaces.
Features of virtual private networks (VPNs) are: Encrypted communications between computers, allowing remote workers to connect to the company network when working from home.
Private communication within a VPC and AWS services is enabled by AWS PrivateLink. By using the interface VPC endpoints, AWS IoT Core is integrated with AWS PrivateLink, allowing you to establish private IoT Core data endpoints inside your VPC. Communication between your VPC and AWS IoT Core for LoRaWAN is entirely and securely conducted within the AWS network when using a VPC interface endpoint.
The security of the IoT solutions improves as AWS IoT Core credential provider endpoints are created in your VPC. The private cloud offering from AWS is called the Amazon Virtual Private Cloud or the Amazon VPC.
The remote IoT VPC Review Raspberry Pi offers an extensive summary that offers a deep overview of the remote IoT VPC service from Amazon Web Services.
Here's a table detailing the key distinctions between the four major classifications of IoT applications, along with the two major criteria used to distinguish them:
| Application Classification | Description | Distinguishing Criteria (1): Data Generation & Processing | Distinguishing Criteria (2): Security & Privacy Requirements | Examples |
|---|---|---|---|---|
| Consumer IoT | Focuses on devices used by individuals in their homes or daily lives. | Typically generates relatively small amounts of data; processing often occurs on the device or in the cloud. | Moderate security and privacy requirements; data is often personal and sensitive. | Smart home devices (e.g., smart thermostats, security cameras), wearables (e.g., fitness trackers). |
| Commercial IoT | Used by businesses to improve operations, enhance customer experiences, and generate revenue. | Generates moderate to high volumes of data; processing may occur on the device, at the edge, or in the cloud. | High security and privacy requirements; data may involve customer information, financial transactions, or sensitive business processes. | Smart retail (e.g., inventory management, customer analytics), connected vehicles, digital signage. |
| Industrial IoT (IIoT) | Deployed in industrial environments to monitor, control, and optimize manufacturing processes, infrastructure, and other industrial applications. | Generates very high volumes of data; real-time processing is often required at the edge or in the cloud. | Extremely high security and privacy requirements; data may involve critical infrastructure, sensitive industrial processes, and safety-critical systems. | Predictive maintenance, remote monitoring of equipment, process automation, smart grids. |
| Infrastructure IoT | Pertains to the use of IoT devices within public infrastructure. | Variable data generation based on the specific application; data may be processed at the edge or in the cloud. | High security and privacy requirements to protect sensitive infrastructure data and ensure public safety. | Smart traffic management systems, environmental monitoring, smart city initiatives (e.g., smart streetlights). |